10 Alerts and Visualizations for S3 Server Access Logs to take control of AWS infrastructure
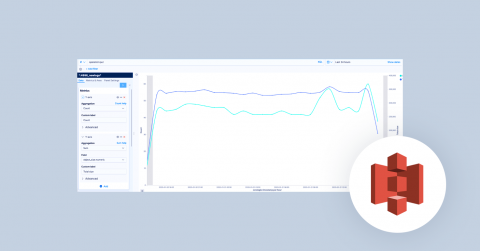
AWS S3 Server Access logs provide detailed records for requests made to S3 buckets. They’re useful for many applications. For example, access log information can be useful in security and access audits. It can also help generate customer insights and better understand your Amazon S3 bill. Coralogix makes it easy to integrate with your S3 server access logs via a Lambda function.