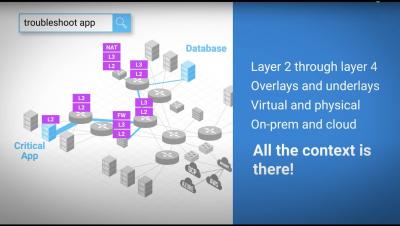
New Advanced AlienApps for Fortinet
Here at AT&T Cybersecurity, we feel strongly that security should fit into your business, not the other way around. We lower the friction security brings to day-to-day operations through automating the essential security operations such as detection and response. By integrating different security products together to form a consolidated security architecture, companies can be protected with less effort.