Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
Wi-Fi Management Added into WatchGuard Cloud Enabling MSPs to Simplify Security Service Deployments Across the Company's Full Technology Portfolio
5 Signs You Have the Remote Access VPN Blues
As the pandemic wears on, and return to work plans continue to shift and morph, there’s really never been a better time to re-evaluate how your organization is handling remote access. Your hastily put-together VPN setup may have gotten the job done in the early days of lockdown, but is it really ready to protect a hybrid workforce that’s now used to flexibility and choice? Here are five signs that it might be time to reconsider your remote access VPN.
The Callback is Coming From Inside the House
Overcoming Segmentation Hesitation
Today, information has surpassed oil as the foremost economic driver in the world. Attempts to steal valuable data have risen dramatically in recent years and will only continue to increase. In response, network segmentation has become a valuable tool to protect data and limit the blast radius of any incidents that do occur.
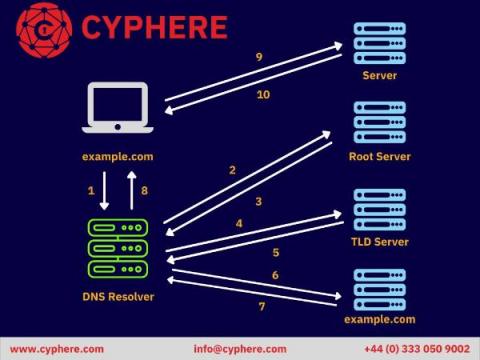
What is DNS hijacking? Redirection Attacks Explained (and Prevention)
Almost everybody in this world uses the Internet. Some use it for work, some for education, some to stay connected with the world and their loved ones, some for shopping, and some use it to browse the world wide web in their leisure time. DNS Hijacking or DNS redirection attacks are a widespread security threat many DNS servers face in today’s modern digital world.
Forward Networks Wins "Enterprise Cloud Computing Software of the Year" Award in 2021 Mobile Breakthrough Awards Program
Take the Corelight challenge: Splunk's Boss of the SOC
Looking for some threat hunting and incident response practice that's more game than work? Check out the new Capture the Flag (CTF) challenges from Corelight, now available on Splunk’s Boss of the SOC (BOTS) website - just in time for.conf! Our two on-demand BOTS modules will show you how Corelight data in Splunk can accelerate your processes and help analysts spend more time analyzing and less time fumbling with queries and gluing together data sources.
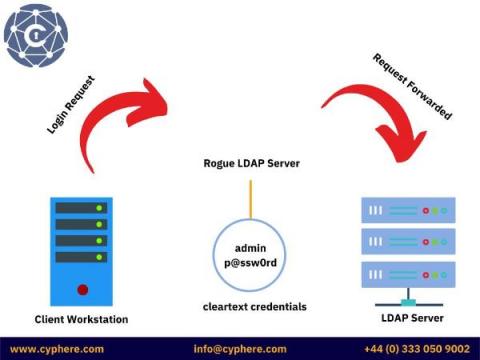
What is Microsoft Local Administrator Password Solution (LAPS)?
Over the time, we have seen passwords being leaked regularly, and the majority of these passwords are common words or words with a simple combination of numbers and special characters, which makes the hashes of such passwords easier to crack.