Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
Make the Headlines for Good News - Not a Security Mishap Due to Config Drift
The risk of config drift is ever present. And when you consider that modern enterprises have incredibly complex and ever-changing networks with thousands of devices, from routers to firewalls to switches, running billions of lines of config, it’s easy to understand why. Networks are constantly being changed by people - who though well intentioned - make mistakes. A configuration change that accomplishes the immediate goal may take the network out of compliance, but how would anyone know?
WatchGuard Cloud Adds New Endpoint Security Modules to Further Strengthen its Unified Security Platform
Enhancing AT&T SASE with Palo Alto Networks 'as a Service'
A few months ago, I wrote a blog on “SASE as a Service” that described how managed services providers (MSPs) can be a catalyzing force for transforming to SASE and bridging the gap between networking and security teams. Since then, AT&T has released a series of managed SASE offers that bring together intelligent networking and cloud-based security in support of our customers.
Do I need a VPN? How a virtual private network can protect you online
A virtual private network (VPN) is a useful tool that protects your online activity by creating a secure ‘tunnel’ that sits between your device and the site or service you’re trying to access.
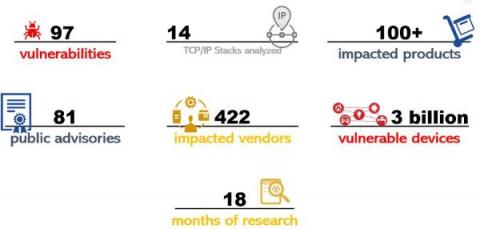
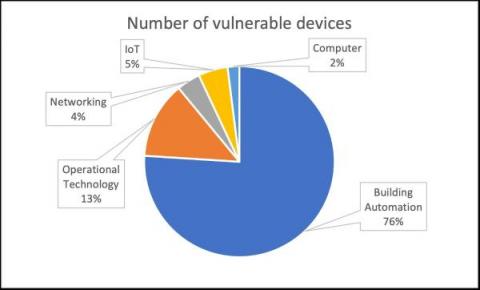
Forescout Research Labs concludes Project Memoria - Lessons Learned after 18 months of vulnerability research
Project Memoria is the largest study on the security of TCP/IP stacks. The idea for this project emerged in May 2020 while collaborating with JSOF on Ripple20. Our researchers understood that the problem with TCP/IP stacks was much deeper and more widespread than initial research had suggested. We hypothesized that similar issues to those identified in Ripple20 could be present in other stacks as well.
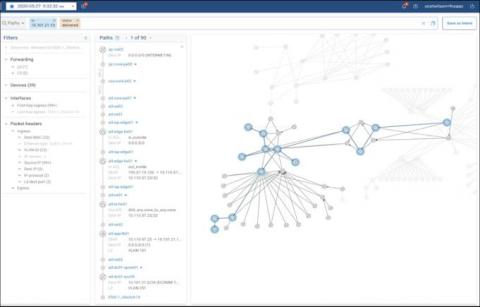
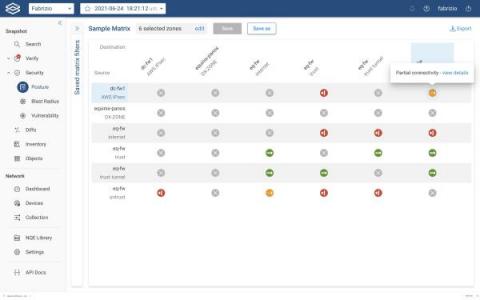
Where is Your Zone-to-Zone Connectivity Matrix?
If you’re like most of the complex IT shops we talk with, you probably don’t even have a current security matrix to store anywhere – file cabinet or data folder. The connectivity matrix is essentially the company security posture, but almost no one has a comprehensive way to visualize and easily understand the connectivity status between the various configured security policies (zone-to-zone policies).
Titania Launches New Module for Organizations Working with U.S. Government Agencies to Meet Cybersecurity Compliance Accurately
New Critical Vulnerabilities Found on Nucleus TCP/IP Stack
Forescout Research Labs, with support from Medigate Labs, have discovered a set of 13 new vulnerabilities affecting the Nucleus TCP/IP stack, which we are collectively calling NUCLEUS:13. The new vulnerabilities allow for remote code execution, denial of service, and information leak. Nucleus is used in safety-critical devices, such as anesthesia machines, patient monitors and others in healthcare.