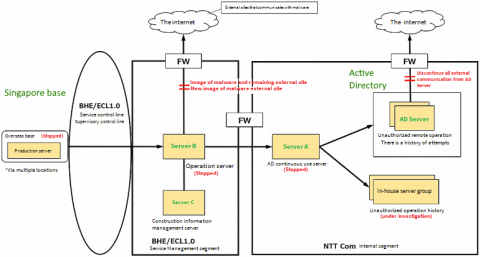
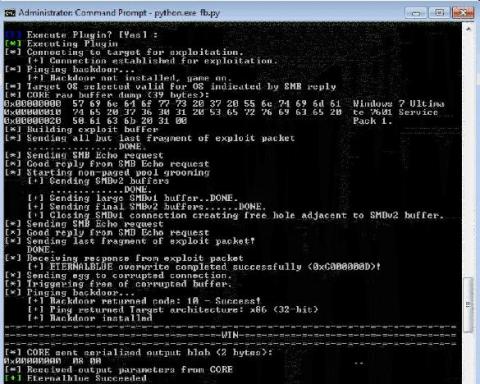
Role of SOAR for Managed Service Security Provider (MSSP)
In the world of digital warfare, internet security has become a daunting task. Cybersecurity threats and attacks; even state-sponsored cyber-attacks are to the fore. Therefore, achieving effective cybersecurity without a few knowledgeable security practitioners and sophisticated toolset is out of the question. We should not depend so much on many security analysts in the age of automation and orchestration.