Preventing malicious use of Weave Scope
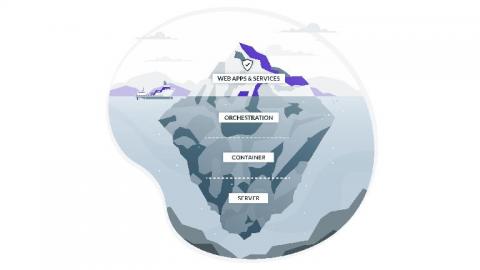
Intezer and Microsoft reported on Sept. 9 that TeamTNT hackers are deploying Weave Scope in compromised systems as an auxiliary tool in their intrusions. Weave Scope is a legitimate and powerful tool to manage server infrastructure that, once deployed, makes it easy to control all resources. In this article, we will describe how this tool can be used maliciously, and how to add specific checks in your security set up to look for it.