Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Malware
State of Ransomware: Caught between perception and reality
Stolen Passwords and Ransomware Attacks: How Small Businesses Can Protect Themselves
Stolen passwords and compromised credentials are among the leading causes of ransomware attacks. In 2021, the IC3 received 3,729 complaints identified as ransomware, with more than $49.2 million in adjusted losses. Startups and small business enterprises (SMEs) must take preventative measures to lower their risk of a ransomware attack. Keep reading to learn more about ransomware and what steps your company can take to protect itself.
The recovery: How to overcome a malware attack
A report published by Cybersecurity Ventures predicts that by 2031, ransomware will attack a business, individual, or device every two seconds. The consequences of such an attack extend beyond the leak of sensitive information and financial losses; customers and clients don’t want to do business with organizations that neglect security of customer data. You can’t simply hope an attack will never happen.
Increase Internet Security While Browsing Online With Proper Antivirus - Top 3 Picks
CrowdStrike Falcon Platform Achieves 100% Ransomware Prevention with Zero False Positives, Wins AAA Enterprise Advanced Security Award from SE Labs
The CrowdStrike Falcon platform delivered 100% ransomware detection and protection with zero false positives in winning the AAA Enterprise Advanced Security (Ransomware) Award in the first-ever SE Labs EDR ransomware evaluation.
How Egnyte Uses AV-Service to Detect Malware
In hybrid or remote desktop environments, content is the most exposed type of data. Egnyte’s all-in-one platform makes it simple and easy for IT to manage and control a full spectrum of content risks, including accidental data deletion, data exfiltration, privacy compliance, and much more. All while giving business users the tools they need to work faster and smarter—from any cloud, any device, anywhere.
Your Cybersecurity MVP: the Rubrik Ransomware Response Team
Have you ever asked yourself, “What happens if I am attacked by ransomware?” Well, the over 4,500 Rubrik customers around the world have the ultimate peace of mind knowing their data is secure with our Zero Trust Data Security platform. In addition to Rubrik’s industry-leading and comprehensive data security solution, we also have a specialized Ransomware Response Team to provide world-class support and care when our customers are attacked.
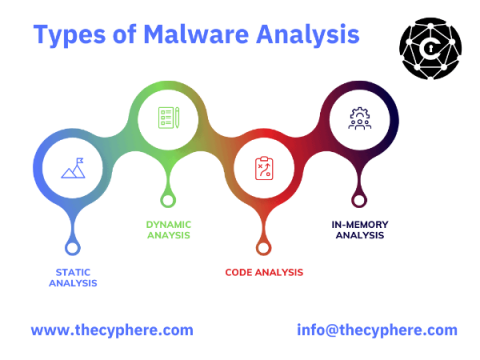
Malware Analysis Guide: Types & Tools
Malware analysis is a process of identifying and examining malware samples to understand the threat they pose. This information can develop defences against the malware or help remove it from infected systems. Malware analysis is a critical skill for incident responders and IT professionals. There are a variety of malware analysis tools and techniques that can be used, depending on the type of malware sample.
Playing Hide-and-Seek with Ransomware, Part 2
In Part 1, we explained what Intel SGX enclaves are and how they benefit ransomware authors. In Part 2, we explore a hypothetical step-by-step implementation and outline the limitations of this method. Watch this live attack demo to see how the CrowdStrike Falcon® platform and the CrowdStrike Falcon Complete™ managed detection and response team protect against ransomware.