Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Malware
Conquer the Three Battlegrounds of Modern Business Continuity and Disaster Recovery
One of the most empowering documents in an organization’s arsenal is its business continuity and disaster recovery (BCDR) plan. Sure, it lays out in detail everything bad that could happen to your business, but it also provides point-by-point strategies to respond to each of those threats. Or does it? A good BCDR plan is a living document that evolves alongside the threats its organization faces. The trouble is that the world is changing fast, and BCDR teams are breathlessly trying to keep up.
Archive Sidestepping: Self-Unlocking Password-Protected RAR
Trustwave SpiderLabs’ spam traps have identified an increase in threats packaged in password-protected archives with about 96% of these being spammed by the Emotet Botnet. In the first half of 2022, we identified password-protected ZIP files as the third most popular archive format used by cybercriminals to conceal malware.
Rubrik and GraphQL - Episode 6 - Using the Rubrik API Code Capture Extension
Despite Lowest Software Flaw Frequency, Manufacturing's Fix Times Lag and Create Ransomware Risk
In 2021, manufacturing became cybercriminals’ most targeted industry as a surge in global ransomware attacks disrupted manufacturing operations and exacerbated supply chain woes. This put even more pressure on manufacturing organizations that were already feeling the heat. Recognizing that ransomware attacks can stem back to software vulnerabilities, many manufacturers are exploring ways to strengthen their software security programs.
Infrastructure Security is Not Enough to Defend Against Ransomware
Register Now Let’s face it, you’re still vulnerable to ransomware. Even if it feels like you’ve done everything—you’ve built a robust defense, you have multiple cybersecurity measures in place, and you’ve implemented a company-wide security training. But, is it enough? Every business is vulnerable to ransomware. From the largest bank to the smallest school.
Why Auto Dealers Are Prime Targets for Ransomware Attacks
Cybersecurity Insights: Secure Your Clients Against Ransomware
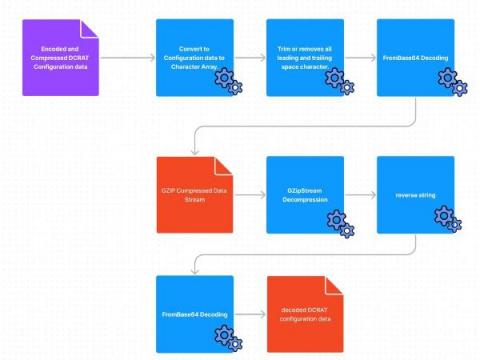
Dark Crystal RAT Agent Deep Dive
The Splunk Threat Research Team (STRT) analyzed and developed Splunk analytics for this RAT to help defenders identify signs of compromise within their networks. Remote Access Trojans (RATs) are one of the most common tools used by threat actors as a malicious payload to attack targeted hosts and steal information. One example is the Dark Crystal RAT (DCRat) that is capable of remote access, post exploitation and data exfiltration.
Stories from the SOC: Feeling so foolish - SocGholish drive by compromise
SocGholish, also known as FakeUpdate, is a JavaScript framework leveraged in social engineering drive by compromises that has been a thorn in cybersecurity professionals’ and organizations’ sides for at least 5 years now. Upon visiting a compromised website, users are redirected to a page for a browser update and a zip archive file containing a malicious JavaScript file is downloaded and unfortunately often opened and executed by the fooled end user.