Joe Biden's Security Order: What it Means for DevOps
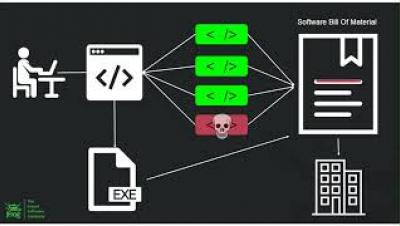
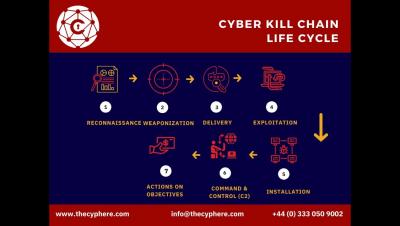
What the Executive Order says today Anticipated further actions by the White House Reasons the software bill of materials (SBOM) will become the source of truth Differences between a SBOM and an “ingredients list” How tools and methods will position developers for success How securing and certifying processes - not just components - may be the key to future compliance