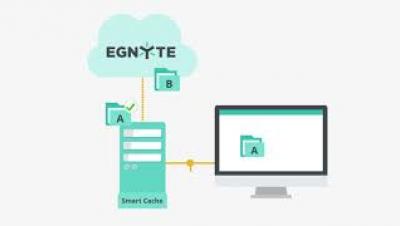
Ransomware Attacks in 2021 And How To Prevent Them
In the last two years, ransomware attacks have drastically increased, and their impact on the organization has become bigger. Bitdefender reports that ransomware attacks increased by 485% in 2020. In this video, we will review what is a ransomware attack and how it spreads across the organization's assets, as well as what types of companies usually get hit by attackers, and how to minimize the risk of getting infected.