Splunk SOAR Feature Video: Playbooks
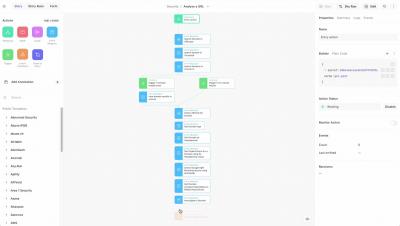
Splunk SOAR playbooks automate security and IT actions at machine speed. Playbooks execute a sequence of actions across your tools in seconds, vs hours or more if you perform them manually. Splunk SOAR comes with 100 pre-made playbooks out of the box, so you can start automating security tasks right away. Splunk SOAR’s visual playbook editor makes it easier than ever to create, edit, implement and scale automated playbooks to help your business eliminate security analyst grunt work. *Users can build and edit playbooks in the original horizontal visual playbook editor, or the vertical visual playbook editor introduced in August 2021.