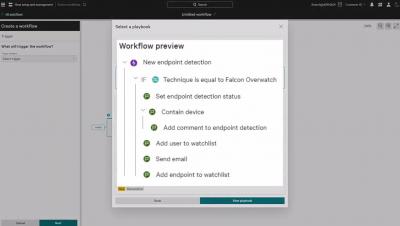
Create Automated Workflows with Pre-Built Falcon Fusion Playbooks
CrowdStrike Falcon Fusion is an extensible framework built on the Falcon Platform that allows the orchestration and automation of complex workflows. These workflows can be used to simplify tasks, accelerate response time, and save valuable time for security teams. Falcon Fusion is included in the Falcon platform and available to all customers. Available in console now are Falcon Fusion playbooks. Playbooks are pre-built workflow templates centered around common use cases.