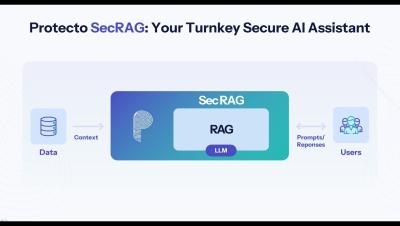
Introducing Protecto's SecRAG, the game-changer for secure AI. SecRAG stands for Secure Retrieval Augmented Generation, a turnkey solution. No need to build complex rag or access controls from scratch. Protecto provides a simple interface and APIs to connect data sources, assign roles, and authorize the data. In a few minutes, your secure AI assistant will be ready. When users ask your Protecto-powered AI assistants, Protecto applies appropriate access control to find the right data and generate responses that don't expose other sensitive information that the user is not authorized to see.