Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest Videos
ScreenConnect Compromise: Hackers Are Watching, Are You Ready? | Threat SnapShot
We know threat actors use RMM tools for command and control and to blend in with other legitimate activity in networks. But how about exploiting RMM tools for fun, profit, and remote code execution? In this week's Threat SnapShot, we'll look at two recent vulnerabilities in ConnectWise ScreenConnect (CVE-2024-1708 and CVE-2024-1709) an authentication bypass and directory traversal that can be combined together to achieve remote code execution.
Fetching data using the Rubrik Security Cloud PowerShell SDK
Already pulled down the Rubrik Security Cloud PowerShell SDK and wondering why you aren't seeing all of the fields you are used to? This video will walk you through the various methods of fetching data from the RSC platform using the SDK. You'll get a basic understanding of how the module is architected and the difference between the autogenerated core cmdlets and the handcrafted wrapper cmdlets that exist within the Rubrik Security Cloud PowerShell module.
#103 - A better way forward for cybersecurity with Maxime Lamothe-Brassard, Founder of LimaCharlie
In this episode of The Cybersecurity Defenders Podcast, we delve into an innovative, engineering-centered perspective on cybersecurity with Maxime Lamothe-Brassard, the Founder & CEO of LimaCharlie. As part of the Canadian Intelligence apparatus, Maxime worked in positions ranging from development of cyber defence technologies, Counter Computer Network Exploitation, and Counter Intelligence. Maxime led the creation of an advanced cyber security program for the Canadian government and received several Director’s awards for his service.
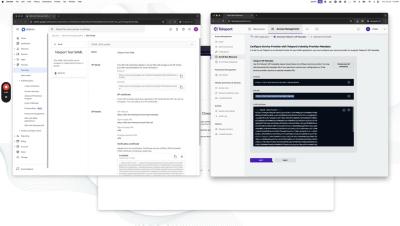
Okta & SCIM Integration with Teleport 15
Join Trent as he introduces the groundbreaking integration of Okta and SCIM with Teleport 15, enhancing identity management and system provisioning. In this comprehensive guide, we delve into how SCIM (System for Cross-domain Identity Management) simplifies the provisioning of users and resources across system boundaries, eliminating the need for ad-hoc mechanisms like webhooks.
New Desktop Access Improvements in Teleport 15
Dive into the essential desktop access enhancements with Teleport 15 in this quick overview. Learn about the performance boosts and user interface improvements that make accessing desktops smoother and more intuitive. Upgrading your Teleport components is key to unlocking these benefits, ensuring a seamless and secure connection experience. What's New.
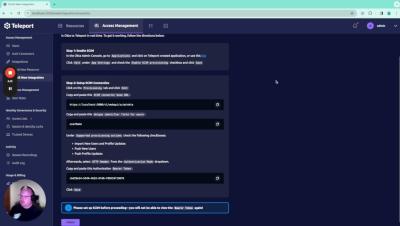
AWS KMS Integration for Teleport
AWS KMS integration for Teleport. With this feature, we can now store cryptographic key pairs in AWS KMS, enhancing our security posture. I'll show you how to set it up for a new cluster and explain the benefits. No action is required from you, but it's important to be aware of this new capability. Let's dive in!
Cyber Trends in Identity and Access Management with Simon Moffatt || Razorthorn Security
Hello Razorwire listeners! It's your host Jim here, and in today's fascinating episode, we sit down with cybersecurity veteran Simon Moffatt. With two decades under his belt in the dynamic field of identity and access management, Simon unpacks the complexities of cyber protection in our modern age. From the evolution of technology to the murky waters of liability and insurance in cybersecurity, Simon's insights shed light on the challenges and trends we face.
New features in Teleport Connect 15
In this insightful video, we explore the latest enhancements to desktop access in Teleport 15, showcasing how these improvements significantly boost performance and usability. With Teleport 15 deployed, we dive into the critical updates, including the necessity of upgrading your Teleport proxy, auth server, and Windows agent to leverage the full potential of these advancements.
PCI DSS v4 0 Readiness - Are you Ready for Ver 3 2 1 Retirement?
Join us for an insightful webinar hosted by VISTA InfoSec, featuring our esteemed panelist, Nitin Bhatnagar, a certified member of the PCI SSC. This webinar is designed to prepare you for the upcoming retirement of PCI DSS v3.2.1 and the introduction of PCI DSS v4.0. PCI DSS safeguards credit card data. With v3.2.1 retiring and v4.0 launching, businesses must grasp these changes and ready themselves for the shift.