Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Adding Multiple Watermarks to Protect IP in Microsoft Office Documents
Cyber Attacks and Data Breaches Cited as the Number One Business Risk for Organizations
Even when looking at the various kinds of risks to business, cyber attacks still remain the biggest problem. But new data shows there may be a lesson to be learned to minimize losses. Aon’s Global Risk Management Survey, nearly 3,000 organizations across 61 countries were asked about sources of business risk. In the report, “Cyber Attack/Data Breach” was the #1 current risk and #1 future risk seen by organizations.
Leveraging OpenAPI as a Core Element of API and Application Security
How to Seize FSMO Roles
Shifting a Flexible Single Master Operations (FSMO) role from one domain controller (DC) to another is normally done through a role transfer operation. But if the DC that holds an FSMO role experiences a serious failure that takes it out of service, you must instead seize its FSMO roles and reassign them to a functioning DC. For example, you need to seize an FSMO role if the current role holder: Important: After you seize an FSMO role from a DC, ensure that it is never reconnected to the network.
Unlock the Power of Your SIEM with Co-Managed SOC
Security information and event management (SIEM) systems play a pivotal role in cybersecurity: they offer a unified solution for gathering and assessing alerts from a plethora of security tools, network structures, and software applications. Yet, the mere presence of a SIEM isn't a magic bullet. For optimal functionality, SIEM systems must be appropriately set up, governed, and supervised round-the-clock.
Strengthening Cybersecurity Resilience: Key Insights from the 2023 ISC2 Cybersecurity Workforce Study
In the fast-paced world of cybersecurity, the recently released 2023 ISC2 Cybersecurity Workforce Study paints a bright future for the industry although significant obstacles remain including a workforce and skills gap. Conducted by ISC2, the leading nonprofit member organization for cybersecurity professionals, this study examines critical aspects of the cybersecurity landscape.
Phishing Defense: Train Often to Avoid the Bait
Surveys, unfortunately, show that the vast majority of organizations do little to no security awareness training. The average organization, if it does security awareness training, does it once annually, likely as part of a compliance program. It is not enough We know from customer data collected, involving many tens of millions of records, over 10 years, that the more frequently an organization does training and simulated phishing, the better able their staff is able to spot phishing attacks.
Nearly Every CIO Identifies at Least One Cyber Threat as a Risk to their Business
When 97% of CIOs all see things the same way, it’s probably a sign to take the risk of cyber threats seriously – a problem new data shows is only going to get worse in the next five years. I cover a ton of reports from cybersecurity vendors on our blog, but when you see a network infrastructure vendor put out a report with intent on just covering the challenges organizations are facing and they have some interesting data on cybersecurity, it got my attention.
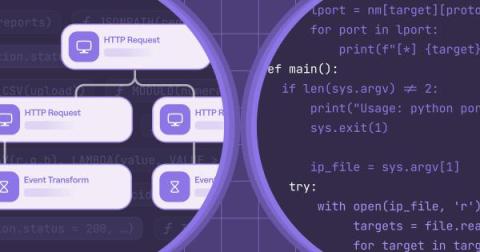
Tines vs Python: Understanding alternative approaches to automation
We're sometimes asked, "Can you run Bash or Python scripts natively in Tines?" and today, we're sharing the answer, and weighing in on the debate between full-code, low-code and no-code automation. The short answer is yes, you can run scripts and linux commands natively in Tines, however, you might not necessarily want to. Many of our customers avoid doing so for security, usability and performance reasons. Let's take a closer look at some of these potential pitfalls.