The 2023 ISC2 Cybersecurity Workforce Study Delves into Cloud Security and AI
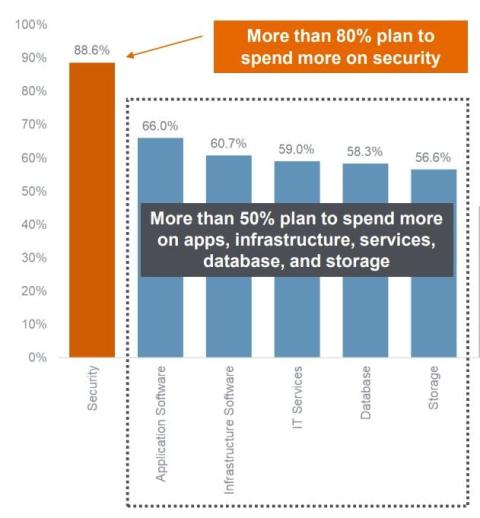
The security industry is at a critical juncture. Capturing the state of affairs is a recent report released by the International Information System Security Certification Consortium, or ISC2.