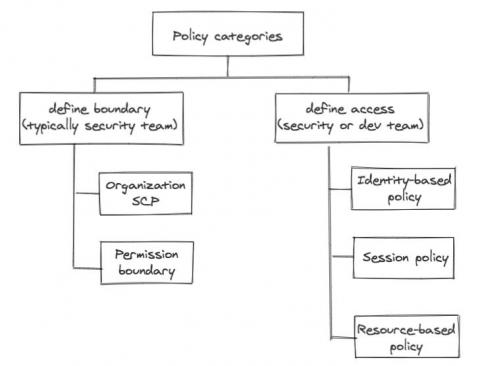
AWS IAM in a layman's terms
We alluded in one of our previous posts that the development team will own a lot of responsibility defining application related resource access control, simply because the dev team owns the infrastructure as code (IaC) responsibility themselves. No matter how security-savvy and security-educated a development team is, the central security team still needs some control, some kind of “trust but verify”.