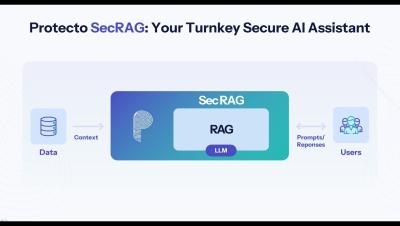
The EU AI Act Explained: Implications for Your Business
The European Union’s Artificial Intelligence Act emerged at the end of 2023 as a landmark law for the digital age and for the regulation of artificial intelligence. It is the world’s first comprehensive AI legislation to govern the ethical development and safe use of AI technologies. The “EU AI Act,” as it’s known, strives to impose a balanced framework as businesses automate manual tasks and deploy AI algorithms to drive efficiency and innovation.