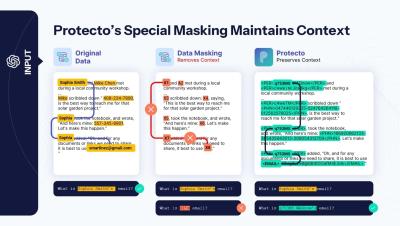
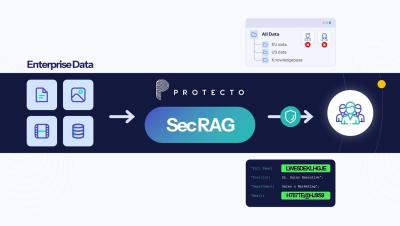
Why You Can't Use Generic Data Masking with AI?
Tired of inaccurate LLM (/RAG) responses because of data masking? Generic masking destroys data context, leading to confusion and inaccurate LLM responses. Protecto's advanced masking maintains context for accurate AI results while protecting your sensitive data.