Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
Your Ultimate Social Media Security Checklist [2022 Updated]
Social media is both a boon and a bane. While it has connected billions of people, made them more accessible, and created more possibilities for the end-users. There's no doubt that it has also made them more susceptible to security threats and vulnerabilities. According to We Are Social, there are around 4.62 billion active social media users worldwide. This is precisely the very reason why cyber criminals love social media as well.
The role of AI in Cyber Security
As artificial intelligence (AI) becomes more and more prevalent in society, it is also making its way into the world of cyber security. AI can be used in a number of ways to help improve cyber security, including by automatically detecting and responding to threats, improving network efficiency, and helping to identify vulnerabilities. In this blog post, we will discuss some of the ways that AI is changing cyber security and how it can help your business stay safe online.
Five tips to jumpstart your SaaS hiring efforts
Hiring is hard. If you're a remote company like we are, you already have a head start. A larger pool of applicants, more practical benefits over a "fun office", etc. That doesn't mean that when the time comes to hire for a new role, you will immediately find the perfect candidate. When we were hiring for our recent frontend developer role, we were surprised how hard it ended up being. Not for lack of candidates, but instead for the right fit within our existing team.
Democratizing Data Using a DataFabric & How it Benefits IT Enterprises
Use Keeper Connection Manager to Automatically Discover & Connect to AWS EC2 Instances
One of the selling points of cloud computing is the ability to quickly spin up new machines as needed. Unfortunately, this means that cloud environments grow very complex, very quickly – and manually updating configuration files to add new instances gets really old, really fast. It’s easy to make a mistake, which inhibits productivity and causes security issues, especially when accessing machines remotely.
Microsoft Discovers Security Flaws In Pre-installed Android Apps
Four high-severity vulnerabilities have been exposed to the framework used by pre-installed Android system apps with millions of downloads. Fixed by Israeli developer MCE Systems, this issue could allow an attacker to launch remote and local attacks or be used as a vector to exploit extensive system privileges to obtain sensitive information. Here’s what Microsoft 365 Defender Research Team had to say about it.
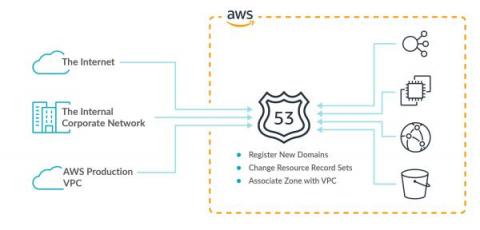
How to Secure AWS Route 53 with Sysdig
Either through human error or intentionally, configuration changes in the cloud may suddenly increase your attack surface. AWS Route 53 is an example of a service that needs to be continuously tracked for risky changes. As the first line of defense of our cloud, it is necessary to secure Amazon Route 53 and monitor risky configuration changes to avoid unwanted surprises. As you probably know, AWS Route 53 is of course a very popular DNS service offered by AWS, with millions of top-level domains.
SMB Guide to Cloud Security
Like their larger counterparts, small- and medium-sized businesses (SMBs) are moving swiftly to migrate IT workloads to the cloud, hoping to slash operating costs, eliminate technical debt, and accelerate digital transformation projects. However, cloud migration security risks are often poorly understood at the outset or overlooked entirely.
AWS Security Best Practices
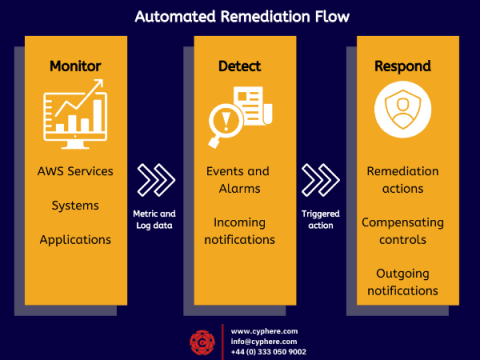
Using security best practices helps businesses establish a security baseline and protect their AWS infrastructure from potential risks. By implementing these practices, companies can reduce the likelihood of data breaches, leaks, and other threats. Additionally, using security best practices can help businesses detect and respond to threats more quickly and effectively.