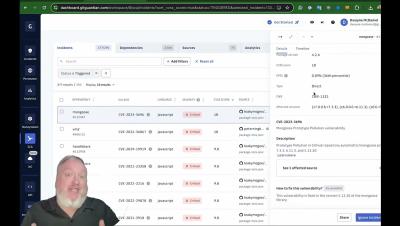
Introducing GitGuardian Software Composition Analysis, further expanding the capabilities of our code security platform. You have long known GitGuardian for secrets detection and remediation, honeytokens, and IaC scanning. Now, with GitGuardian SCA, you can effortlessly scan your applications to detect known vulnerabilities introduced through both Direct & Transitive dependencies. The platform will automatically prioritize incidents depending on their context and help developers find the best path to remediating any issues.