Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Windows
Endpoint Security: More Than Just Windows Machines
How to Perform Windows Registry Repair: Registry Repair Windows 10
The Windows registry is a database that contains important information about your computer — users, preferences, applications, attached devices and much more. The Windows operating system constantly refers to the registry; for example, to open a program, install new software or change your hardware, Windows must check the values of certain registry keys.
The Windows Restart Manager: How It Works and How It Can Be Hijacked, Part 1
Malware utilizes a multitude of techniques to avoid detection, and threat actors are continuously uncovering and exploiting new methods of attack. One of the less common techniques includes the exploitation of the Windows Restart Manager. To stay ahead of malicious authors, it is important to be aware of them and understand how they work.
Protecting your Windows Fleet with Zero Trust
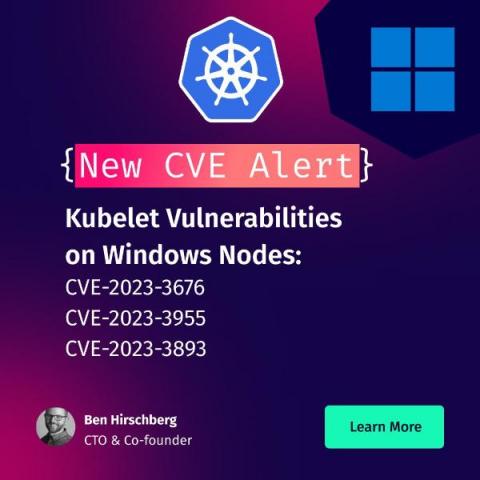
Kubelet vulnerabilities on Windows nodes: CVE-2023-3676, CVE-2023-3955 and CVE-2023-3893
Windows Server 2012 End of Life
Windows Server 2012, is the sixth version of the Windows Server operating system by Microsoft, as part of the Windows NT family of operating systems. At the time, Windows Server 2012 brought forth an array of enhanced features and refinements, and over the years, it stood as a cornerstone for many organisations, providing a bedrock of reliability, scalability, and adaptability to accommodate applications and workloads.
Windows Security: Detailed Guide to Understand Security Baselines
The security of your organization’s data and systems is at the top. As a leading provider of operating systems and applications, Microsoft understands the criticality of safeguarding its customers’ sensitive information. With products like Windows, Windows Server, Microsoft 365 apps for enterprise, and Microsoft Edge, they strive to offer secure solutions that inspire confidence.
Windows Remote WMI Security Primer for the Faint-Hearted
Local WMI querying is straightforward to implement and troubleshoot — but remote WMI querying is another story. Indeed, setting up secure remote WMI querying for a user with no admin rights is a daunting task. This blog can help. I’ll walk you through the steps I used to enable a standard domain user to query the Microsoft SQL Server WMI namespace class on a Windows Server 2012 R2 running Microsoft SQL Server 2016.