Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Securing Access to Production MySQL Databases.
MySQL brands itself as the world’s most popular open source database. As popular as MySQL database is among developers and SQL enthusiasts, it is equally popular amongst hackers. Misconfigured server access, overprivileged roles, and weak authentication schemes are the most common security issues in MySQL database. While access control features provided by MySQL are adequate enough at the SQL level, it is error-prone to manage access at the operational level.
Ransomware Has Evolved, And So Should Your Company
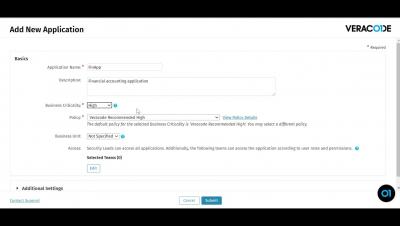
Create a New Application Profile in the Veracode Platform
Yuba County Survived a Ransomware Attack and Lived to Tell the Tale
Estée Lauder Uses Rubrik to Manage and Protect Global Data at Scale
Fortifying Cyber Defense: How to Act Now to Protect Global Supply Chains
Four Steps to Modernizing Government Cybersecurity with Zero Trust based on the Executive Order
The pandemic has accelerated digital transformation and telework on a scale never seen before. Employees are working from anywhere and collaboration in the cloud has skyrocketed. But this new environment has expanded the cyber attack surface, compromising critical U.S. infrastructure and lives of our citizens. The recent slew of major cyber attacks including SolarWinds, Microsoft Exchange and Colonial Pipeline, has moved cybersecurity improvements to the top of the agenda for the U.S.
How the Elastic InfoSec team uses Elastic Security
At Elastic, we internally use, test, and provide feedback on all of our products. For example, the Information Security team is helping the Product team build a stronger solution for our customers. The InfoSec team is an extremely valuable resource who acts not only as an extension of Quality Assurance/Testing, but also as a data custodian.
How Cloud Evangelists Face - and Overcome - Cloud-Computing Security Challenges
This is the third in a series of posts examining the recent Devo research report, Beyond Cloud Adoption: How to Embrace the Cloud for Security and Business Benefits, which is based on a survey conducted by Enterprise Strategy Group (ESG). This time, we’ll take a look at the cloud-computing security challenges Cloud Evangelists face. Let’s begin by explaining how we define that group.