Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Important Data Privacy Questions You Should Be Asking Now
The Bot Problem Why is it Necessary to Mitigate Bot Threats
Web Application Security Checklist
Securing the Digital Supply Chain Ep. 10 - Peeyush Ranjan
Veracode Named A Leader In The 2022 Gartner® Magic Quadrant For Application Security Testing For Ninth Consecutive Time
Meeting PCI DSS Third-Party Risk Requirements
Organizations must enact effective third-party risk management (TPRM) programs to ensure their vendors fulfill cybersecurity requirements. Otherwise, they risk carrying the financial and reputational harm caused by customer data breaches. The PCI DSS standard covers aspects of third-party risk management as it's applicable to all organizations that process credit card data, especially the heavily regulated finance industry.
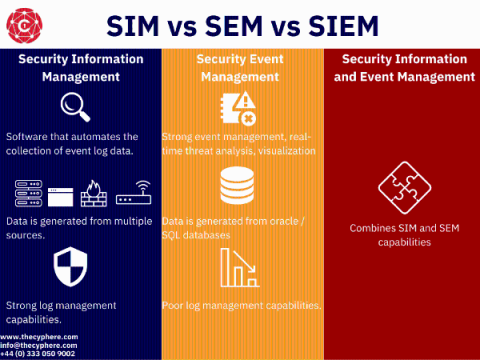
What is SIEM? A guide to cyber Security Information and Event Management
Security information and event management refer to Security Information Management (SIM) and Security Event Management (SEM) through a single pane of glass. SIEM solutions are used by security analysts to monitor any potential threats within the infrastructure of their organisation.
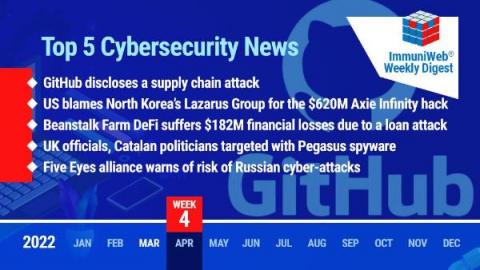
GitHub: Hackers Breached Multiple Orgs Using Stolen OAuth User Tokens
Read also: the US blames North Korea’s Lazarus Group for the $620M Axie Infinity hack, Beanstalk Farm suffers $182 million financial losses due to a cyber-attack, and more.