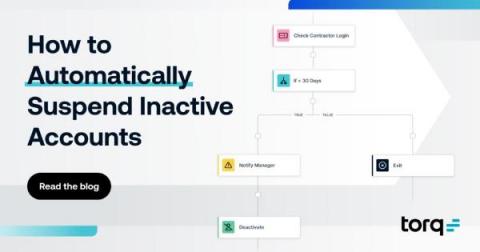
How to Automatically Suspend Inactive Accounts Using Torq
Contractors, freelancers, and other temporary workers have become essential parts of the modern enterprise. For IT and security teams, these individuals present unique challenges compared to full-time workers—and potential risks. The ‘offboarding’ process for these contractors is often less formal than bringing them on. Meaning, many just stop using their entitlements and accounts without actually closing them. These dormant accounts can pose serious risks to the organization.