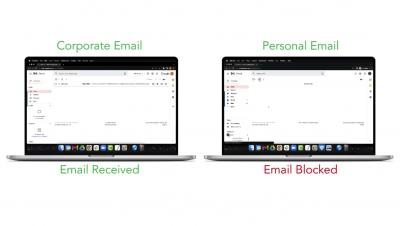
Enhancing Security with AI/ML
Digital transformation has driven the rapid adoption of cloud-delivered services like SaaS/IaaS/PaaS in enterprises. This, in turn, has resulted in the migration of digital assets (aka data) from the confines of enterprise data centers to the cloud data centers that are not under the control of the enterprises. Additionally, the onset of the COVID-19 pandemic has resulted in remote work becoming the norm.