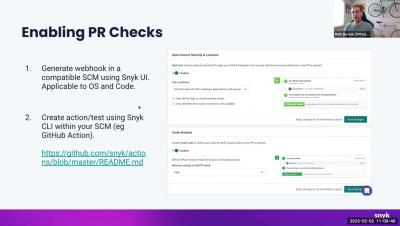
Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Tracking the transport of radioactive sources with blockchain
This week, Australian authorities recovered a tiny capsule, just 6mm x 8mm (0.24 x 0.31 inches) along a 900km section of Australia’s longest highway, the Great Northern Highway. The pea-sized capsule was a radiation gauge containing caesium-137, a radioactive material with a half-life of 30.05 years, that is used to measure the density and flow of materials in the mining, and oil and gas industries.
Why Bots Threaten Your Cybersecurity
Secrets Need to be Secured Everywhere Not Just in Code Repositories
Organizations are unaware of the prevalence of API keys and secrets throughout their systems, and how their users are sharing and using them. Even with security best practices and policies in place, the lack of awareness or compliance, as well as the possibility of human error means that API keys and secrets need protection regardless of where they are stored or shared.
AppSec Decoded: Takeaways from the 2022 "Software Vulnerability Snapshot"report | Synopsys
Difference to Know: Cyber Security, Software Security, Application Security
Did you know that when we talk about online security, cyber security, application security, and software security are all different? Sometimes, software security and application security are used interchangeably. However, there is a key difference between these two; both are different from cyber security. Application security is a more reactive approach and software security, on the other hand, has a more proactive approach.
How to Become a Cybersecurity Analyst [Complete Guide]
A cybersecurity analyst, also known as an information security analyst, specializes in the security of networks and IT infrastructure. The role of cybersecurity analyst has a relatively broad job description, offering great opportunities for individuals looking to enter the cybersecurity industry and branch out into various cyber-related career paths.
Startup and Stability, Surprisingly now in the Same Sentence?
These are uncertain times in tech. If you’re at one of the many companies in the news recently, think back to why you joined. Was it the people? The tech? Or maybe… the perception of a rock-solid, not-going-anywhere, totally-guaranteed position? Things have changed lately.
Trust me, I'm an engineer - Escaping the traps of social engineering
Biggest Data Breaches You Need To Know About
Data breaches exposed at least 42 million records between March 2021 and February 2022. With the increasing risks associated with the cyber world, this comes as no surprise.