Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Your DPO Questions Answered
Every business that collects personal data via a website, app, or even via the phone/post will find that they need the skills and expertise of a Data Protection Officer at some point to ensure safe and confidential data processing. But what is a DPO exactly? Do you really need one? And what if you don’t want to hire someone full time? Read on to find out more about the roles and responsibilities of the DPO and when to hire one to secure your data.
Lacework's Andreas Schneider: How to adapt as a CISO and the value of security failures
In this episode of the Future of Security Operations podcast, Thomas interviews Andreas Schneider - the Field CISO EMEA at Lacework. Leveraging its data-driven platform and cloud-native application protection solution, Lacework helps organizations make sense of immense amounts of security data with minimal effort.
Why Cybersecurity Training and Courses Should Be Mandatory in Healthcare Education?
Earlier, even prior to the digitalization of healthcare records, it was still easier to keep the information secure and private. Records were in the physical form and could be protected in many ways. Now that people can pull up their entire health histories with the press of a few buttons, things are very different. With the information now being stored and processed online, the threat and risk exposures are equally high. So, to address such threats the U.S.
CrowdStrike 2023 Global Threat Report: Resilient Businesses Fight Relentless Adversaries
The CrowdStrike 2023 Global Threat Report, among the most trusted and comprehensive research on the modern threat landscape, explores the most significant security events and trends of the previous year, as well as the adversaries driving this activity. The latest edition of the CrowdStrike Global Threat Report comes at a critical time for organizations around the world.
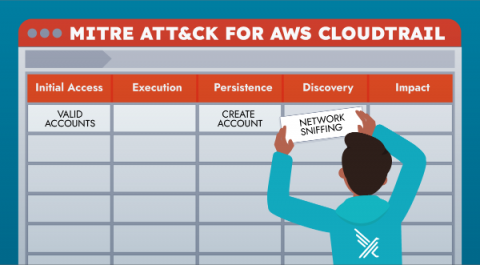
Aligning Falco's Cloudtrail Rules with MITRE ATT&CK
This blog will explain how Falco’s Cloudtrail plugin rules can be aligned with MITRE ATT&CK Framework for Cloud. One important note is that the team at MITRE has developed several different matrices to address the unique risk associated with adversaries in the cloud, in containerized workloads as well as on mobile devices.
SCARLETEEL: Operation leveraging Terraform, Kubernetes, and AWS for data theft
The Sysdig Threat Research Team recently discovered a sophisticated cloud operation in a customer environment, dubbed SCARLETEEL, that resulted in stolen proprietary data. The attacker exploited a containerized workload and then leveraged it to perform privilege escalation into an AWS account in order to steal proprietary software and credentials. They also attempted to pivot using a Terraform state file to other connected AWS accounts to spread their reach throughout the organization.
Responsible disclosure: Access control vulnerability discovered in the ThingsBoard IoT platform
On December 2022, a security researcher from the Outpost24 Ghost Labs team discovered a vulnerability on the ThingsBoard IoT platform, where a normal user’s privileges can be escalated, by doing a simple post with an additional header, and exploiting the associated flaws, to take control over the entire platform and related accounts. Upon reporting of the vulnerability to the vendor, it was quickly resolved.
Five key data privacy trends for 2023
With growing volumes of personal data being collected, analyzed, shared and stored, there is more expectation than ever on businesses to ensure privacy for their employees, clients and wider supply chain. The digital age has streamlined ways of working, improved the targeting and personalization of services and communications and made detailed information available at the touch of a screen. But personal data is exactly that – personal.
Voter ID Verification API: Streamlining User Onboarding using simplified Identity Verification
The Election Commission of India issues the Indian Voter ID Card (officially known as the Elector’s Photo Identity Card (EPIC)) to adult Indian citizens who have reached the age of 18. It is primarily used for identity proof of Indian citizens when they cast their votes in local, state, and federal elections held in the nation. It may also be used for identity verification of name, address, and age verification for other needs like getting a SIM card for a phone or applying for a passport.