Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
What is CIRCIA? How This Law May Affect Your Business
The Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) of 2022 is a US federal law that requires all critical infrastructure entities to report any cybersecurity incidents or ransomware attacks to the Cybersecurity and Infrastructure Security Agency (CISA) within a specified timeframe.
The Differences Between SOC 2 vs. ISO 27001
SOC 2 and ISO 27001 are compliance frameworks commonly required of organizations that house data or store sensitive information. Both standards focus on information security management, but they have some key differences in their approach and scope. Let’s take a closer look at the differences between SOC 2 and ISO 27001, and see if one or both are right for your organization.
Meet Mick England: The DPO that Led Robin's SOC 2 & ISO 27001 Compliance
Out of his 29 years of cloud and security experience, Mick has been with Robin for 6, leading their internal compliance operations and making sure that their customers’ data is secure. Robin needed to get SOC 2. They also wanted a way to answer security questionnaires faster. Continue on to see how Mick was able accomplish both.
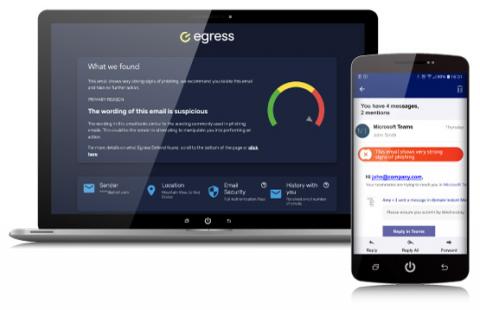
Detecting AI-generated phishing emails with Egress Defend
With the launch of ChatGPT, concerns have been growing around the use of AI in phishing. The concerns are founded: AI can write phishing emails. It’s not the only tool in a hacker’s toolkit either - cybercriminals can use many different technologies to build a phishing campaign and send phishing emails. Many, like chatbots, are widely available for consumer and business use.