Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
VMware ESXi Servers: A Major Attack Vector for Ransomware
In our new threat briefing report, Forescout’s Vedere Labs provides details on the recent ransomware campaign targeting VMware ESXi virtualization servers, or hypervisors, and analyzes two payloads used in these attacks: variants of the Royal and Clop ransomware. We also present the tactics, techniques and procedures (TTPs) used by attackers in this campaign, discuss mitigation recommendations and list indicators of compromise (IOCs) that can be used for detection or threat hunting.
New Content Preview Feature Results in up to 90% Productivity Increase
The Nightfall platform is lauded by customers for its high accuracy detection of sensitive data across a variety of cloud environments. This helps users save time by only surfacing the most relevant and most critical instances of sensitive data exposure. We’re always looking for ways to continue to build value in this area, and many of our feature updates like our new PHI detector and enhanced secrets detection releases accomplish this.
Demystifying SIEM migration: Pitfalls to avoid and tips for ensuring success
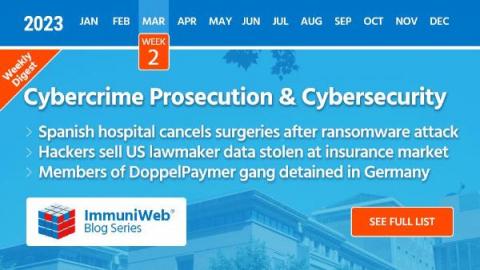
The Hospital Clinic de Barcelona Forced to Cancel Hundreds of Surgeries and 3,000 Patient Checkups Due to a Ransomware Attack
Read also: Indian crypto exchange BitBNS hid a $7.5M breach, hackers are selling US lawmaker data, and more.
The Impact of Code Signing on Your Organization
When it comes to releasing software, many organizations take software signing lightly. But they don’t know that not signing a software or not using a Code Signing Certificate can have an adverse impact on the organization. A non-signed application is not only a risk for end-users, but also for the software publisher. And when you sign a software, it offers multiple benefits that positively impact the organizational goals. To understand it more thoroughly, let’s move further.
Behavioral Analytics Explained: How Analyzing (Odd) Behavior Supports Cybersecurity
Five key takeaways from Outpost24's Cyber Resilience Day
True to its theme ‘Cyber Resilience’, our recent cyber security gathering was able to dissect the fast-moving threat landscape with insights and information nuggets from a panel of security experts and practitioners on the shortcomings and the need for better use of threat intelligence. Here are five takeaways from the Cyber Resilience Day in Breda co-hosted with our customer CM.com and a panel of cybersecurity experts.
Modern SOCs and MDR services: Modern SOC Key Functions
At a high level, the SOC's core mission remains to help the enterprise manage cyber risk, but what has changed is the sophistication of cyber threats and the mechanics of the SOC to operate. To successfully protect and respond to threats, SOCs need deep visibility into organization activity and automate key but repetitive functions while freeing analysts to focus on more valuable functions such as threat hunting and vulnerability management.