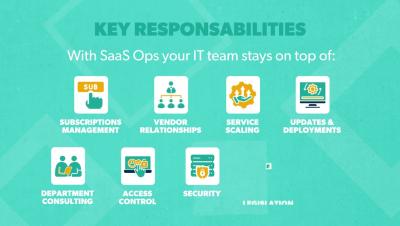
What is Software-as-a-Service (SaaS) Operations?
In this video, learn the following key points about Software-as-a-Service Operations (SaaS Ops): Resources and social media: Transcript: Organizations rely on SaaS applications more and more to get things done. But with so many specialized apps and different vendors, IT departments can get lost in the cloud. It’s easy to see why -- most organizations use over 100 SaaS apps in their day-to-day tasks. For an IT team, that’s a ton to manage.