Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Risk Management
'One-Stop Shop' Functionality with Global Search
There are many critical factors to ensuring an effective cybersecurity program; however, two of the most important are accuracy and timeliness. With limited search capabilities that direct you to insufficient results or extended navigation time to find items of relevance, the cyber risk of your rapidly growing vendor ecosystem is left unmanaged. Think about it like this: when you have two contacts in your phone saved under the same first name, how do you determine which one is the right one to call?
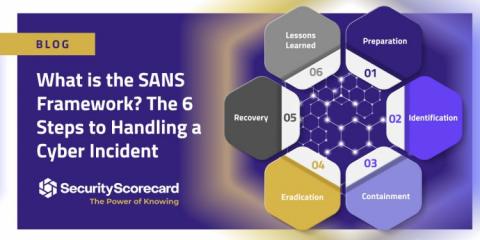
What is the SANS Framework? The 6 Steps to Handling a Cyber Incident
A cyber incident can range from a minor power outage to a full-scale cyber attack. No matter the incident scale, having clear guidelines to follow can help organizations create effective and standardized response plans. The SysAdmin, Audit, Network, and Security (SANS) Institute is one of the leading organizations providing cybersecurity training, research, and certification.
Brady Technologies Announces the Sale of its Commodities Business to STG
Top 4 Emerging Trends in Telecom Risk Management
The telecom industry is continuously evolving as laws governing the industry change, providers join new markets, and the expansion of cellular connections continues to grow. And since the global pandemic of COVID-19, millions of people around the world have relied on the availability of network services to work in addition to keeping in contact with their loved ones.
New: SecurityScorecard Extension for Chrome
Here at SecurityScorecard, our mission is simple: To make the world a safer place. This mission necessitates that we embrace trust, transparency, and security. In furtherance of this mission, today we released our first-ever Chrome Extension. With the new SecurityScorecard Chrome Extension, you can automatically see the simple A-F security rating of the websites you visit, enabling you to evaluate the risk of the sites you visit before supplying your data to them.
5 Steps to Selecting a Vendor Risk Management Framework
Third parties are an inevitable and essential part of your business ecosystem. They’re your vendors, partners, and contractors. They improve efficiency, extend your reach, and make it possible to deliver the best possible products and services. From a security perspective, however, they also bring a significant amount of risk. Misconfigurations of a third-party’s cloud can lead to supply chain data breach risks.