Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
January 2024
Office Hours with Jack Freund, PhD - Monthly Product Review
Why the future of AppSec is ASPM from Snyk AppRisk
How to Automate and Streamline Vulnerability Management Processes
What Are the Similarities and Differences Between FISMA vs. FedRAMP Certification?
Obrela's Starwards Party Highlights
Building a Scalable Third Party Risk Management Framework
Customer Testimonial: Horiens Reduces Supply Chain Risk With SecurityScorecard
Manual GRC: Why Spreadsheets Are Not the Solution
What Are Compliance Automation Tools?
Risk Mitigation in Retail: A Guide to E-commerce Cybersecurity
Five worthy reads: Making AI functionality transparent using the AI TRiSM framework
Building a Business Case for Investment in TPRM Software
What is a Cyber Security Audit vs. Assessment (And Which One You Need)
Risk Management in Network Security: 7 Best Practices for 2024
Risk Management Essentials: How to Build A Risk Register
Introducing Risk Analytics
SecurityScorecard Returns to the World Economic Forum's Annual Meeting: Our Top 5 Insights
Introducing SecurityScorecard MAX
6 Behaviors that Hinder Vulnerability Management Maturity
Cybersecurity Maturity Model Implementation - A How-To Get Started Guide
Riscosity Achieves SOC 2 Type II Compliance
How to Detect Shadow IT and Hidden Risk in Your Organization
All You Ever Wanted to Know About FedRAMP 3PAOs
Cybersecurity and Proxy Season: What Business Executives and Risk Leaders Need to Know
Audit Log Best Practices For Information Security
Addressing Third-Party Risk in 2024: Insights Inspired by Bitsight-Google Study
Determining Cyber Materiality in a Post-SEC Cyber Rule World
Europe's Regulatory Environment to Drive Automation in GRC
What is a Compliance Risk Assessment?
How Automated Compliance Can Reduce the Cost of Compliance
15 KPIs & Metrics to Measure the Success of Your TPRM Program
Introducing Vendor Discovery
The Need For a Shift Up Strategy, Using CRQ for Resilience, Part 3
Trust Assurance for Security Teams: A 6 Point Scorecard for Upgrading Your GRC Program
Release Spotlight: Orca Connector
API Risk Management: A Strategic Approach to API Risk Reduction
Why you should automate your third-party risk management
The number of tools organizations use is growing everyday. According to Zylo 2023 SaaS Management Index Report, the average organization has 291 SaaS applications in their tech stack — a number which only increases as your organization grows. The more tools that are added to your tech stack, the more third-party risk your business incurs. These risks could result in threats like data theft, service outages, or loss of revenue and customer trust.
Volt Typhoon's Recent Compromise of 30% of Cisco RV320/325 Devices
How to Perform a Network Security Risk Assessment in 6 Steps
What Is Cyber Risk Quantification (CRQ)?
The Need For a Shift Up Strategy, Using CRQ for Resilience, Part 2
Keeping a Pulse on All Third-Party Connections
The core tenets of information security is to protect assets from unauthorized disclosure, prevent unauthorized changes, and to make them available as needed. These align with the CIA security triad of Confidentiality, Integrity, and Availability.
Building a Shadow IT Policy: What CEOs, CTOs, and CISOs Need to Know
Top 9 Cyber Risk Scenarios That Can Lead to Financial Loss in 2024
A RiskInsiders' Guide to PCI DSS v4.0 Compliance: Key Changes and Deadlines
7 Cybersecurity Frameworks That Help Reduce Cyber Risk (List & Resources)
While security ratings are a great way to demonstrate that you’re paying attention to the standard cyber health of the organization, you also need to show that you’re adhering to industry and regulatory best practices for IT security and making informed decisions for the long-term. A cybersecurity framework can help.
Cyber Exposure Management Meets the New SEC Reporting Requirements
How To Calculate Cybersecurity ROI and Communicate It to Executives
Introducing the Cyber Resilience Scorecard
This week at the World Economic Forum Annual Meeting, SecurityScorecard published the first Cyber Resilience Scorecard, offering leaders and decision-makers a comprehensive and global view of global cyber risk. SecurityScorecard identified a strong correlation between a country’s cyber risk exposure and GDP, which underscores that a nation’s economic prosperity is deeply intertwined with its ability to navigate the complex landscape of cyber threats.
Compliance Automation and Its Benefits for Reporting
What Are the 12 Requirements of PCI DSS?
Unpacking New SEC Regulations with Industry Experts
TPRM Risk Analytics
Identifying Blind Spots Through External Attack Surface Management
Optimizing Returns from Your Cyber Risk Program
Unlock the Power of Attack Surface Management with Insights from a KuppingerCole Analyst
The Security Performance Management Evolution: Interview with Bitsight's Greg Kesen & Dark Reading
CRQ Journey Part 3: Communicable, Calibrated, Granular Results
Shadow IT: Managing Hidden Risk Across Your Expanding Attack Surface
Understanding Data Lineage and Data Provenance
Data lineage and data provenance are related terms, but different. Lineage focuses on the origins and movements of data over time, while provenance focuses on the transformations and derivations of data from original sources. Provenance helps teams to follow the source of data and verify its authenticity, surfacing any potential risks or vulnerabilities. In other words, lineage is more about “where” data travels, and provenance is more about the “what” of data history.
Unpacking New SEC Cyber Regulations with Industry Experts
Threat Intelligence Research
As part of our effort to make the world safer, SecurityScorecard has been tracking threat actor groups conducting cyberattacks on behalf of nation states.
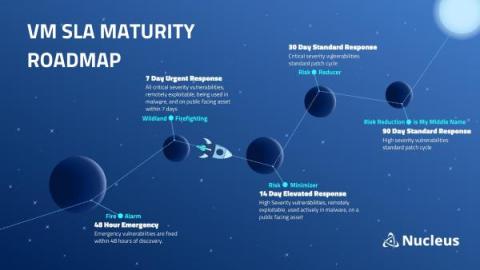
How to Adapt Vulnerability Management Service Level Agreements (SLAs) to Team Maturity
ShadowIT, Hidden Risk, and the insights that drive action to reduce exposure
The Need For a Shift Up Strategy, Using CRQ for Resilience, Part 1
Shadow IT, Hidden Risk, and the insights that drive action to reduce exposure
The Essentials of Cyber Security Risk Management
Vendor Discovery: Automating identification of third party relationships
Data Insights on AgentTesla and OriginLogger Victims
Automating Extension Risk Assessment and Permissions
Using Amazon SageMaker to Predict Risk Scores from Splunk
Introducing Security Ratings for Telecommunications, Internet Service Providers, and Cloud Providers
Telecommunications, Internet Service Providers, and Cloud Providers are some of the most critical sectors on the planet. They enable global connectivity, provide access to a wealth of information in real time, and transform business operations. As the foundation of modern communication, these industries have ushered in countless innovations and propelled society forward.
Exposure Risks with File Transfer Protocol (FTP)
Bitsight Delivers Enhanced Analytics on IT Infrastructure Service Providers
5 Compliance and Governance Happenings That Will Drive Exposure Management in 2024
The Apache Log4J Vulnerability: Questionnaire & VRM Tips
5 Considerations for an Effective Healthcare Risk Management System
The healthcare industry is no exception to the rapid levels of transformation we’re seeing across multiple industries right now. As more facilities begin to leverage electronic health records (EHRs) and internet-connected medical devices for patient care, organizations are becoming more reliant on advanced technologies. While these changes have helped advance patient care in many ways, they have also introduced the healthcare sector to greater levels of risk.
Analyzing the Biggest Cybersecurity Exposure and Threat Events from 2023
Quantify Cyber Materiality When Navigating APRA's Regulations
Cloud Monitoring: Critical for Business Success
The Most Important Security Metrics to Maintain Compliance: Best Practices for Prioritizing Cyber Resilience
WatchGuard Endpoint Risk Assessment Demo - How to Activate It
What is a Cybersecurity Assessment?
Routine cybersecurity assessments are a crucial component of a holistic risk management program. Your organization must keep an eye on the cyber hygiene of its entire ecosystem, including third- and fourth-party vendors, at all times. A cybersecurity risk assessment allows you to do this by identifying the cyber risks that affect your security posture, which leads to more informed decision-making on how best to allocate funds, implement security controls, and protect the network.
3 Steps Government Policymakers Can Take to Reduce Critical Infrastructure Cyber Attacks
Domain (in)security: the state of DMARC
How to Resolve Google Safe Browsing Risks
How to Perform A Cybersecurity Risk Analysis in 2024
Risk analysis is defined as the process of identifying, reviewing, and analyzing any existing or potential cybersecurity risks that could negatively impact a business. Performing a cybersecurity risk analysis helps your company identify, manage, and safeguard data, information, and assets that could be vulnerable to a cyber attack. Such an analysis helps to identify systems and resources, determine the risk, and create a plan for security controls that can help protect your company.