Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
May 2023
An Enterprise Guide: Periodic Cloud Security Risk Assessments
MITRE System of Trust Framework for Supply Chain Security
Supply chain security has been a top concern for risk management leaders ever since the high-profile attacks to SolarWinds and Log4j took place. While there's no one-size-fits-all way to identify, assess, and manage cyber risks in the supply chain, MITRE's System of Trust Framework offers a comprehensive, consistent, and repeatable methodology for evaluating suppliers, supplies, and service providers alike.
Reverse-Engineering Java and JavaScript Malware
Most malware security researchers encounter in the wild is written in C or C++. These languages provide low-level system access and control, plus performance, allowing threat actors to create highly efficient and stealthy code. But that doesn’t mean cybercriminals are limited to those two languages. SecurityScorecard recently reverse-engineered the Vjw0rm worm written in JavaScript and the Java-based STRRAT remote access trojan (RAT).
How Data Integration Benefits Cyber Risk Exposure Management
4 Ways to Reduce Exposure and Manage Risk Across Your Expanding Digital Infrastructure
Digital infrastructure is the foundation of a modern, connected organization. It encompasses connectivity, cloud, compute, security, storage, applications, databases, IoT, remote networks, and more. Once housed on premises, this infrastructure now extends across regions, offices, work-from-anywhere environments—and across the third-party providers who make digital transformation possible. Securing this digital infrastructure is a growing challenge.
New vulnerability could lead to one of world's most powerful cyber attacks
The other week, Bitsight released a piece of high-profile research alerting the public to a high-severity vulnerability potentially allowing attackers to launch one of the most powerful Denial-of-Service (DoS) attacks in history. Here’s a summary of what happened and why it matters: Security leaders are asking “now what?” and Bitsight has answers.
10 Steps to Take Now to Reduce Supply Chain Risks
Open-source software has been a godsend for the development community. They bring lower development costs, faster application delivery, and greater flexibility; it’s no wonder nearly 90% of modern applications comprise third-party software nowadays. That’s not to say open-source software doesn’t come with its share of pitfalls, including security risks and vulnerabilities.
4 Signs of Incomplete Information Security Risk Management
Minimizing public sector cybersecurity risk
The public sector is critical to national and international security. Yet, new research from SecurityScorecard and the Cyentia Institute found that 61.6% of public sector agencies have open cyber vulnerabilities, taking a median of 309 days to remediate. What’s more, 53% of public sector agencies are losing ground closing their cyber vulnerabilities, due in large part to a greater reliance on third-party vendors with less-than-optimal cybersecurity hygiene.
What You Should Know About the New Cyber Security Evaluation Tool Model
Cybersecurity Audit Checklist
How to Automate Cyber Risk Quantification
How to Identify and Mitigate Digital Transformation Risks
Market pressures and growth opportunities are accelerating digital transformation. According to Gartner, 89 percent of board directors say digital is embedded in all business growth strategies. Meanwhile 99 percent say that digital transformation has had a positive impact on profitability and performance (KPMG). The cloud, connected IoT devices, and remote work capabilities are the cornerstones of digital transformation.
6 Trends to Watch from RSA Conference 2023
The Power of Using Risk Scores to Automate Continuous Conditional Access
Co-authored by David Willis and Gary Jenkins As we wrote in an earlier blog, the concept of cybersecurity risk continues to be codified, qualified, and, finally, quantified. With the rise of RESTful API endpoint support and near-real time telemetry sharing, companies can seize the opportunity to automate the IT/security stack’s response to risky users (in addition to devices, data, and applications—to be covered in future blogs).
Improved risk assessment with EPSS scores in Snyk
The number and complexity of software vulnerabilities is continuously growing. The ability of development and security teams to assess the threat level a given vulnerability poses and prioritize fix efforts accordingly greatly depends on access to as much context as possible about the vulnerability.
What is Cyber Risk Governance?
What is Data Exfiltration? Plus, 3 Tips to Prevent It
When a hacker breaches a network or system, data exfiltration often follows. But what is data exfiltration and how can you prevent it?
Risk Tolerance: Understanding the Risks to your Organization
‘A ship in port is safe, but that's not what ships are built for,’ said Dr. Grace Hopper, Rear Admiral of the US Navy and a computer pioneer. As soon as the ship leaves the harbor, or even the dock, there are risks. Depending on conditions and purposes, the ship's crew might decide they are negligible, that they can be recovered from, or that the potential rewards are worth the risk. The same ideas can be applied to computers.
How to Monitor Your Risk Management Plan
How to conduct a Privileged Access Management risk assessment
In today's business landscape, organizations rely heavily on digital systems, applications, and webpages for their daily operations. However, with the increasing use of technology comes growing risks of unauthorized access to sensitive information and data.
Template: Everything you Need to Craft a Supplier Risk Management Plan
Third-party vendors are a vital part of your business ecosystem. But if you’re not careful, these companies can introduce cyber risk. The SolarWinds supply chain hack is a notable example of the jeopardy that even the most trusted partnerships can yield. But with so many moving parts, creating a supplier risk management plan – and executing on it – can be a challenging and arduous task. According to Gartner, 60% of organizations work with more than 1,000 third-party vendors.
Unveiling the Future of AI in Cybersecurity
Welcome to our latest podcast episode, where we delve into the fascinating realm of AI in cybersecurity. Phil Agcaoili, the esteemed entrepreneur, and former CISO professional, joins us in this fascinating discussion. Alongside our hosts, Max Aulakh and Joel Yonts, we unravel the profound impact of artificial intelligence on cybersecurity, compliance, and the workforce.
How to Secure Your Expanding (and Hidden) Cybersecurity Ecosystem
Your organization’s cybersecurity ecosystem is complex. It covers a wide range of internal digital assets but also extends beyond the network perimeter to other entities, such as vendors, suppliers, and cloud service providers—making you increasingly vulnerable to cyber risk. To secure this ecosystem, you need both an outside-in and inside-out perspective of vulnerabilities and risks.
SecurityScorecard's Partnership with the TSA
As part of our continued commitment to making the world a safer place, SecurityScorecard recently partnered with the Transportation Security Administration (TSA). This partnership will enable the agency to more accurately monitor and assess the cyber health of the nation’s pipeline, rail, and aviation transportation systems.
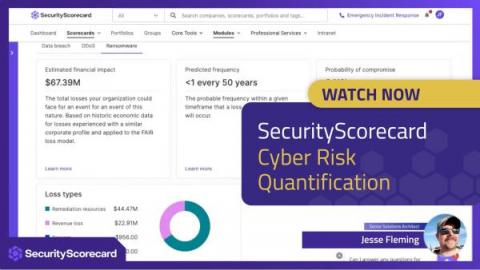
Translate Cyber Risk into Dollars With SecurityScorecard
Cyber risk is not just a security issue, it’s also a business issue. When security leaders and their businesses don’t see eye to eye, resources get misallocated, expectations aren’t met, and businesses are left unprepared to face threats. SecurityScorecard launched its Cyber Risk Quantification product in April 2022, allowing customers to quantify the financial impact of cyber risk and help facilitate collaboration and communication among business stakeholders.
Candid Chats: Does a risk-based approach really make a difference?
In The Clouds: What Can Risk Management Do for You?
Cybersecurity Risks in Hybrid Working Environments
Properly Explaining Risk Appetite to the C-Suite
In the first part of this series, we looked at some common issues when a Chief Information Security Officer (CISO) is communicating with the Board. At the heart of many of these issues is how the CISO and upper management view security. As one CISO recently told me, "It's a catch-22 situation: If the business leaders don't consider this to be a business problem, they are unlikely to listen to people they don't consider to be business leaders telling them it is.".
Updated Fraud Risk Guidance Available
ATO Attacks: What You Should Know About Protection and Prevention
CISO Health and Wellness: An Unconventional Solution to a Systemic Challenge
At a swanky steak house on Manhattan’s Upper West Side, I sat with 100 other security professionals in a dimly lit wood-panelled room, its walls lined with photographs of famous and near-famous patrons. Nearly all of us were at least one cocktail into our evening of high gustation, storytelling, and network building. (Old Fashioneds were the drink of choice that evening).
Top Emerging Cybersecurity Threats (and How to Mitigate Them)
Just as your organization thinks it is prepared, new cyber threats appear. In March 2023, the European Union Agency for Cybersecurity (ENISA) published its list of the 10 top cybersecurity threats to emerge by 2030.
3 Ways "GRC as Usual" Holds You Back
Get Started with SOC 2 for Vendor Risk Management
SOC 2 reports evaluate internal controls to see how well a company identifies, assesses, mitigates, and monitors risks. In the context of third-party risk management (TPRM), a SOC 2 can give you confidence that your critical vendors are following best practices to protect your data. If you’re getting started with SOC 2 for third-party risk management or need an update, this blog has got you covered.
How to Build a Cyber Resilient Framework
Cyber attacks aren’t just on the rise; they are skyrocketing. Incidents of ransomware alone nearly doubled last year. A new study by CrowdStrike finds that ransomware-related data leaks increased by 82% in 2021. Furthermore, ransom demands now average $6.1 million per incident, a 36% increase from 2020. Clearly, reacting to and remediating security threats when they arise is not going to cut it anymore.
Don't Manage Third-Party Risk Alone
New research from the Cyentia Institute found that 98% of organizations do business with a third party that has suffered a breach. The report also found that the average firm has 11 third-party relationships and hundreds of indirect fourth- and nth-party relationships. Bottom line: an expanding attack surface makes companies more prone to cyberattacks.
What is Zero Trust? Everything You Need to Know to Secure Vendor Access
Zero trust is a cybersecurity approach that restricts network access so only the right people are accessing the specific information they need —and nothing more. Here’s everything you need to know about the basic principles of Zero Trust and how to apply them to your third-party risk management program (TPRM) to create more secure remote access connections.
Advantages of End-to-End Security
How cybersecurity's "5 Percent Rule" could help you avoid the next cyber attack
It’s not easy being a cybersecurity leader these days. Security vulnerabilities in software, hardware, and devices are rising in number and severity, bringing with them risk of ransomware, breach, and other dangerous cybersecurity incidents. The risks presented by vulnerabilities are rising fast: Here’s the important question: With cyber vulnerabilities rising and presenting increasingly serious risks, are organizations doing enough to fight back? The answer might surprise you.
Obrela at Delphi Forum || Panel Discussion
Risk Management is a Team Sport with Emilio Escobar
Password Security: How To Protect Credentials Across Your Supply Chain
Many major stories about cyberattacks or data breaches have one weak link in common: passwords. Oftentimes, the simple alphanumeric password that acts as gatekeeper to our personal phones and email accounts is the same one that protects enterprise businesses’ servers. And passwords are only as strong as we make them. Unfortunately, though, most employees—76 percent of Americans, according to research we conducted in 2022—never change their passwords, or only do so when forced to.
Shine a Light on Shadow IT: Vanta Launches Category-First Vendor Risk Management Solution
Cybersecurity Risk Mitigation: Understanding the Limitations of Reducing a £2 Million Risk
Zero day remediation tips: Preparing for the next vulnerability
Businesses increasingly run on software, which, unbeknownst to its developers, can contain vulnerabilities that attackers often discover and exploit before a patch is available. This makes zero day attacks inevitable, but you can reduce their impact in your network and across your supply chain if you’re prepared to act fast.
A Mere Five Percent of Vulnerable Enterprises Fix Their Issues Every Month: How to Help Them Do Better?
Software vulnerabilities are one of the leading threats to an organization's cybersecurity posture, yet recent research from Bitsight reveals that enterprises affected by software vulnerabilities resolve them at a typical compound rate1 of only about 5% per month compounded continuously. However, there is evidence of much faster remediation for certain classes of vulnerabilities.
A new way to proactively manage third-party risk: Vendor Risk Management
Businesses are using more SaaS applications than ever, with an average of 110 apps per organization. This proliferation of third-party applications means increasingly more customer and employee data is handled by external vendors. Ensuring your third-party vendors are secure by tracking risk, conducting reviews, and responding to issues is a security best practice and compliance requirement. Unfortunately, this process is often a manual — and expensive — one.
AI, Cybersecurity, and Emerging Regulations
The SecurityScorecard team has just returned from an exciting week in San Francisco at RSA Conference 2023. This year’s theme, “Stronger Together,” was meant to encourage collaboration and remind attendees that when it comes to cybersecurity, no one goes it alone. Building on each other’s diverse knowledge and skills is what creates breakthroughs.
5 Reasons to Implement Third-Party Risk Management Software
How to Mitigate Supply Chain Attacks
Cybercriminals are sneaky. They know that the weakest link in an organization’s cyber defenses is its supply chain. In fact, supply chain attacks are now the avenue of choice for hackers. Consider the facts.
How Do You Perform a Supplier Risk Assessment?
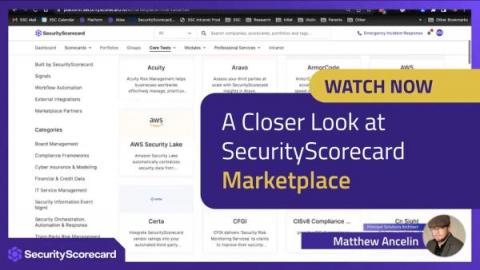
A Closer Look at SecurityScorecard Marketplace
On average, organizations deploy 47 different cybersecurity solutions and technologies. This puts security, IT, and VRM teams in a difficult position, working with various tools that don’t integrate. One-third of organizations identify “non-integration of security tools” as a major roadblock to getting the total value of their investments.
New Study Reveals Shocking Truth About Data Breach Cover-Ups
What is a cybersecurity report? Why are they necessary?
Waves of change are constantly disrupting companies of all sizes around the world, particularly when it comes to cybersecurity. Digital infrastructure keeps expanding, work models constantly change, and the web between businesses gets more and more intertwined. It’s no surprise that CISOs and risk leaders are evolving. A majority of boards now see cyber risk as business risk, so they’re asking hard questions around risk and exposure.