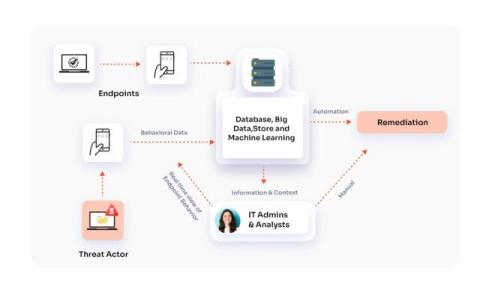
What are the ISO 27001:2022 controls?
ISO published the ISO 27001 standard to outline an information security management system (ISMS) in 2005. Since then, significant revisions have taken place in 2013 and 2022 to better reflect the evolving climate of cybersecurity threats and technologies.