Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
The Top 5 Most Dangerous Cyber Attacks of all Time
Cyber attacks are on the rise, and they show no signs of slowing down. In fact, many experts believe that we are only seeing the tip of the iceberg when it comes to cybercrime. As businesses continue to move their operations online, they become increasingly vulnerable to cyberattacks. In this blog post, we will take a look at the five most dangerous cyberattacks in history. These attacks have caused billions of dollars in damage and affected millions.
Avoid These Employee Monitoring Blunders
In September 2021, 45% of full-time employees were still working remotely, and the trend is hard to reverse. People like the freedom of working from home. Without a commute, they save time. Without a boss looming in the background, they can multi-task at home. And, without an office full of colleagues, they don’t have to worry about dressing up or having water cooler chit-chat. While employees see these changes as positives, businesses see remote workers as a bit of a risk.
OPA for All: Policy as Code in 10 Minutes
Open Policy Agent, or OPA, has emerged as an industry standard for cloud-native authorization and policy as code. From 2018 to now, it has grown from being a Cloud Native Computing Foundation (CNCF) sandbox project into a fully mature, graduated CNCF project, deployed by many of the largest organizations in the world. (For just the tip of the iceberg, here is a list of users who have made their adoption of OPA public).
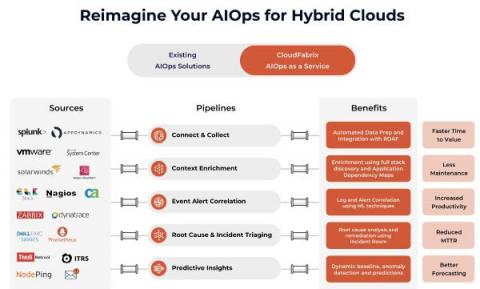
AIOps Feature Byte: How you can Accelerate AIOps Data Integrations with New Robotic Data Automation Fabric (RDAF)
Snyk finds PyPi malware that steals Discord and Roblox credential and payment info
Snyk security researchers continually monitor open source ecosystems for malicious packages, utilizing static analysis techniques to identify and flag suspicious packages. Each malicious package is identified upon publication to the package manager and swiftly added to the Snyk Vulnerability Database. During recent research, the team found 12 unique pieces of malware belonging to the same actor.
Penetration Testing as a Service (PTaaS): the evolution of Penetration Testing at AT&T
Let us start by defining Penetration Testing as a Service (also known as PTaaS) because there are several different definitions and variations being used throughout the industry. Some of the similarities include: This is where AT&T starts to differentiate itself from competitors. This next part we believe to be critical: There is a misconception about Penetration Testing as a Service, that it devalues the quality of testing.
CrowdStrike Wins Technology Innovation Leadership Award, Continues Dominance in Endpoint Security Market
CrowdStrike is proud to receive Frost & Sullivan’s 2022 Global Technology Innovation Leadership Award in the endpoint security sector. This recognition reflects CrowdStrike’s continued investment to drive innovation and deliver more value to its customers through its industry-leading Falcon platform.
3 Important Things to Know About Cookie Security
Security researchers at Feroot are warning application security professionals of the client-side security risk associated with unprotected cookie structures. Because cookies are so ubiquitous with all website types—from e-commerce and banking to social networks and SaaS applications—organizations need to be aware of the privacy and data exploitation risks associated with poor cookie security.
Agentless vs. Agent-based FIM: Which One to Choose?
Malware attacks are escalating. For example, there were 57 million IoT malware attacks in the first half of 2022, a staggering 77% increase year to date. Unfortunately, traditional signature-based antivirus and sand-boxing technologies are insufficient against today’s sophisticated attacks. In particular, advanced persistent threat (APT) viruses, Trojan malware and zero-day malware often evade these defenses.