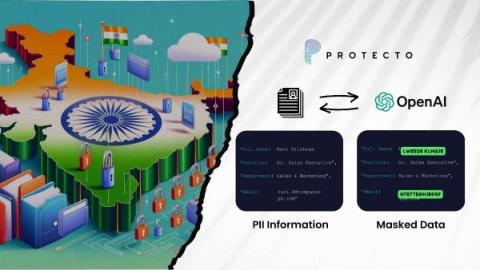
Ensure PII Compliance in India with OpenAI & Top LLMs
India's data protection laws are evolving to safeguard the privacy of its citizens. One crucial aspect is the requirement that Personally Identifiable Information (PII) remain within India's borders for processing. This data residency requirement poses a challenge for businesses that want to leverage powerful AI language models (LLMs) like those offered by OpenAI, which often process data in global centers.