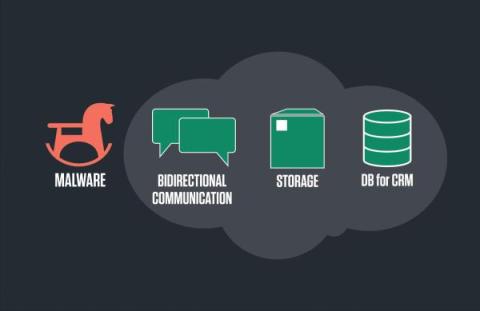
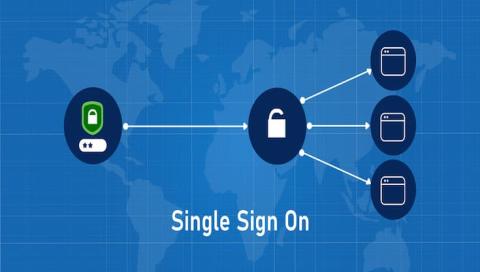
Outsmarting Cyber Threats: Etay Maor Unveils the Hacker's Playbook in the Cloud Era
In an era where cyber threats evolve as rapidly as the technology they target, understanding the mindset of those behind the attacks is crucial. This was the central theme of a speech given by Etay Maor, Senior Director of Security Strategy, of Cato Networks at the MSP EXPO 2024 Conference & Exposition in Fort Lauderdale, Florida. Titled, “SASE vs.