Building a Scalable Permissions Service: Overcoming Challenges in Access Control
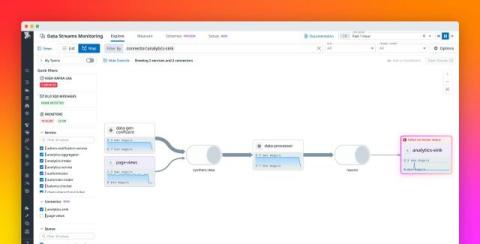
Permissions are at the center of every operation at Egnyte. Every interaction any user has with the system is bound to go through a stringent permission check,be it creating a file, copying it, moving it, sharing it, deleting it or using an operation as simple as adding comments. The permissions model is extremely crucial as without it, data leaks, incorrect access escalations, and unauthorized operations can occur.