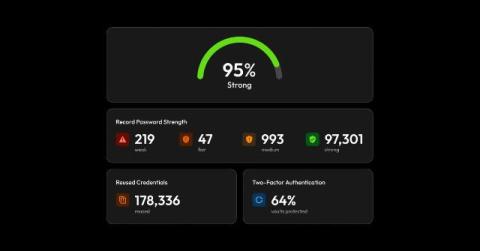
Keeper Improves Security Audit and Browser Extension Functionality
Keeper Security is pleased to announce significant improvements to the Security Audit tab of the Admin Console for business users, as well as the Browser Extension for organizations and individuals alike. The updates include a refreshed User Interface (UI) for both, new functionality to refresh and reset Security Audit scores, the ability to generate a passphrase via the Browser Extension and more.