What is Vendor Tiering? Tips to Improve Your Vendor Risk Management
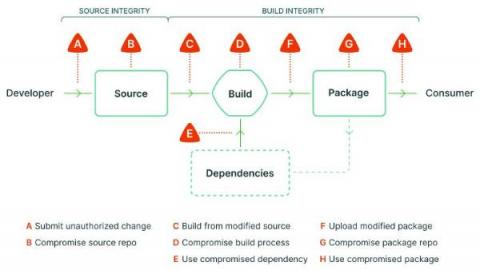
Over the last few years, supply chain attacks have increased in number and sophistication. As companies accelerate their digital transformation strategies, managing third and fourth-party risk and a complete look into their security posture becomes more important to securing data and meeting mission-critical compliance requirements. According to one survey, 60% of security leaders plan to deploy supply chain security measures in 2022.