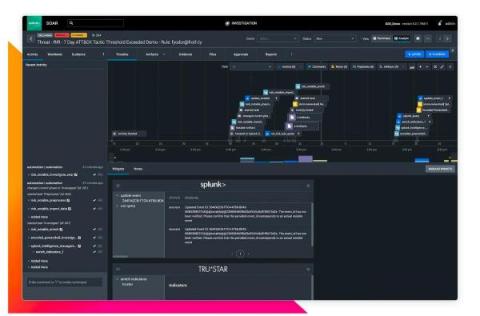
What's InfoSec? Information Security Explained
A major subset of overall cybersecurity, Information Security focuses on protecting sensitive data and information from the risks of cyberattacks. It covers but is not limited to: The fundamental goal of information security is to prevent sensitive data from being compromised by criminals or state actors. InfoSec encompasses a wide range of tasks and practices, spanning from monitoring user behavior to assessing risk to ongoing education.