Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
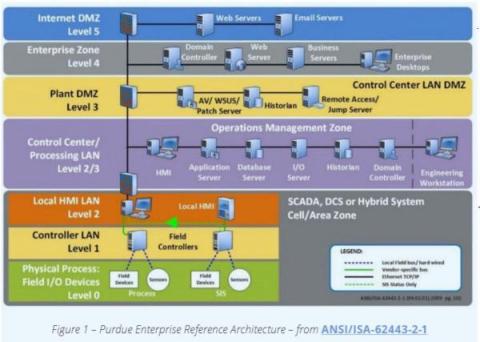
Deep Lateral Movement in OT Networks: When Is a Perimeter Not a Perimeter?
Forescout’s Vedere Labs latest research report is the first systematic study into deep lateral movement: how advanced adversaries can move laterally among devices at the controller level – also known as Purdue level 1 or L1 – of OT networks.
Who's Knocking on the Door? An Overview of Authentication and MFA - And How It Can Uplevel Your Organization's Cyber
Authentication, at its core, is the act of verifying credentials. In the case of human beings, it’s as simple as answering the question, “Who are you, and how do I know for sure it’s you?” Authentication is something we’re constantly engaging with in everyday life.
Hive Ransomware Group - Brought to Justice
The Hive Ransomware Group is a sophisticated criminal organisation that targets businesses around the world with their ransomware attacks. The group’s primary goal is to extort money from victims by locking and encrypting their data, making it inaccessible until a ransom payment is made.
Rubrik Brings Security at the Point of Data to Microsoft Azure Stack HCI
Operating in a cloud model means not only being able to access your data anywhere but that your infrastructure is flexible and scalable enough to accommodate demands that change from day to day or sometimes from moment to moment. This is easy enough to achieve in a public cloud, where resources can be made elastic and added and removed dynamically.
Cryptography 101: Key Principles, Major Types, Use Cases & Algorithms
Social Engineering Attacks: The 4 Stage Lifecycle & Common Techniques
Deconstructing Identity Security
Most companies now recognize the serious and insidious nature of cybersecurity threats. But many fail to grasp that the digital transformation, remote work, automation and cloud migration activities of the last few years have turbocharged the number of identities seeking access to data and critical business systems. This surge in identities has exponentially increased the likelihood of cyberattacks, undercutting the effectiveness of traditional identity and access management (IAM) paradigms.
Eliminate compromised passwords with One Identity Password Manager & Have I Been Pwned
It's a good question, and if you're curious about whether any of your email addresses or passwords were included in a data breach, you can easily find out at HaveIBeenPwned.com. This entirely free service, managed by Microsoft Regional Director & MVP Troy Hunt, lets you enter an email address or password to see how many breaches it has been included in.