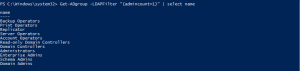
Monitoring domain user accounts with elevated access rights
3Standard users having elevated privileges is never good news. Accounts such as domain admins, enterprise admins, schema operators, krbtgt, administrators, and replicators, are a few privileged user groups within an Active Directory (AD) environment. The AdminCount attribute is an AD attribute set to “1” on privileged user accounts.