Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
What is Virtualization in Cloud Computing
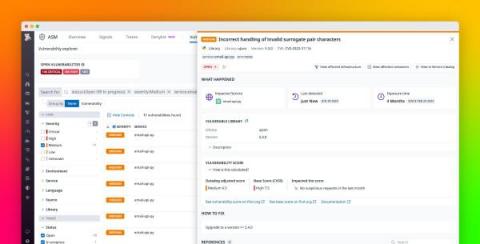
Enhance SBOMs with runtime security context using Datadog Application Vulnerability Management
Software today relies heavily on open source, third-party components, but these reusable dependencies sometimes inadvertently introduce security vulnerabilities into the code of developers who use them. Some of the most serious vulnerabilities discovered in recent years—like the OpenSSL punycode vulnerability, Log4Shell (Log4j), and Dirty Pipe (Linux)—reside in popular open source packages, making them so widespread that they could compromise almost the entire software ecosystem.
AWS WAF vs. Cloudflare
It's Raining Phish and Scams - How Cloudflare Pages.dev and Workers.dev Domains Get Abused
As they say, when it rains, it pours. Recently, we observed more than 3,000 phishing emails containing phishing URLs abusing services at workers.dev and pages.dev domains.
How social media compromises information security
Today’s companies operate in a complex security environment. On the one hand, the threat landscape is growing. Bad actors are becoming more and more refined as they get access to new tools (like AI) and offerings (like hacking-as-a-service). On the other hand, companies are dealing with more sensitive data than ever before. This has prompted consumers and regulators alike to demand for better security practices.
4 Steps to a Comprehensive Security Approach
Software supply chain attacks have become a major concern for organizations in recent years, as cybercriminals increasingly target third-party software components and libraries used to build applications. These attacks can have devastating consequences, including data breaches, theft of intellectual property, and disruption of business operations. In this article, we will explore the growing threat of software supply chain attacks and discuss strategies for mitigating the risks.
SCARLETEEL 2.0: Fargate, Kubernetes, and Crypto
SCARLETEEL, an operation reported on by the Sysdig Threat Research Team last February, continues to thrive, improve tactics, and steal proprietary data. Cloud environments are still their primary target, but the tools and techniques used have adapted to bypass new security measures, along with a more resilient and stealthy command and control architecture.
What is cyber risk exposure and how can you manage it?
How to Augment or Replace Your SIEM with the CrowdStrike Falcon Platform
In Part 1 of our SIEM blog series, we discussed the state of SIEMs today and how CrowdStrike Falcon® LogScale solves five key SIEM use cases while improving security outcomes and cost savings compared to traditional SIEMs. Our conversations with customers have made it clear: SIEM requirements don’t stop at the five use cases covered in that blog. Modern SIEM systems extend beyond log management to deliver full threat detection, investigation and response.