Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
What to Expect When Seeking Cybersecurity Insurance
Cybersecurity liability insurance has progressed dramatically since the first bona fide policies emerged in the late 1990s. Some of the greatest changes that have occurred in recent years include insurance companies no longer insuring against state-sponsored attacks or ransomware events. The insurers do not want to become part of a cyber-war.
The Value of Vulnerability Management
There’s nothing that makes you feel older than realizing how much of your life you have dedicated to a single topic. At what point do you consider yourself an expert? After more than 17 years in vulnerability management, I’m starting to come around to the idea that I might be an expert in the field. Although, the main reason I feel that way is because, at this point, I’ve seen pretty much everything.
Australian Energy Leader Picks Salt for API Security!
We’ve taken our award-winning API security “Down Under” with our latest customer success! Today we announced that Jemena, a leading energy company in Australia, has selected the Salt Security API Protection Platform to protect its critical gas and electricity infrastructure. Here at Salt, we are honored that Jemena has chosen us to secure its API modernization project!
Data Breach Impacts American and Southwest Airlines: US Pilot Credentials Compromised
In a chilling reminder of the relentless threat posed by hackers and cybercriminals, not even the aviation industry is safe from their clutches. Recent reports have shed light on a grave security breach, as unauthorized individuals gained access to vital pilot credentials within two prominent American aviation companies. The far-reaching impact of this breach serves as a stark warning to businesses across all domains: no data is safe from the clutches of malicious actors.
Defend Your Software Supply Chain by Curating Open-Source Packages Entering Your Organization | Announcing JFrog Curation
Modern organizations are constantly striving to gain a competitive advantage by delivering software solutions at a remarkable pace. To achieve this, they heavily rely on open-source software (OSS) libraries and packages, which constitute a significant portion (80-90%) of their software solution. However, while open-source software offers numerous benefits, it also presents potential security challenges.
CTI Roundup: Truebot infects US & Canada networks
Truebot infects networks throughout the US and Canada, Charming Kitten targets new operating systems, and SmugX targets European government entities.
What Is Business Email Compromise?
Business Email Compromise (BEC) is a targeted cyberattack in which a cybercriminal poses as a trusted figure, such as the CEO of a company, and sends out an email to specific individuals requesting sensitive information or money. BEC attacks involve research and preparation in order for the cybercriminal to develop a convincing impersonation. Continue reading to learn more about business email compromise and what organizations should do to prevent this type of attack.
Challenges when implementing an AWS multi-account strategy
Implementing an AWS multi-account strategy is a popular approach that helps organizations to manage their cloud resources efficiently. In my previous post, I discussed our reasons for implementing an AWS multi-account strategy, our journey, and some of the benefits we gained as an organization. However, implementing this strategy can come with its fair share of challenges.
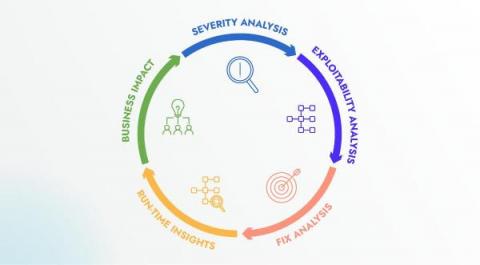
How to Deal with Hundreds of Fixes? Choosing the Right Vulnerability Management Solution
Relying solely on the Common Vulnerability Scoring System (CVSS) is insufficient when it comes to effective vulnerability management. While the CVSS score provides a quantitative measure of a vulnerability’s severity, it fails to capture the contextual nuances that can significantly impact the actual risk to an organization. In this article, we will discuss how best to choose a vulnerability management solution.