Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Proactive Threat Hunting Bears Fruit: Falcon OverWatch Detects Novel IceApple Post-Exploitation Framework
A Quick Guide To Information Security Programs
Broadly speaking, an information security program is a set of activities and initiatives that support a company’s information technology while protecting the security of business data and enabling the company to accomplish its business objectives. An information security program safeguards the proprietary information of the business and its customers. The Gramm-Leach-Bliley Act (GLBA) has a more specific definition of what a security information program should entail.
Server hardening, why should you automate it?
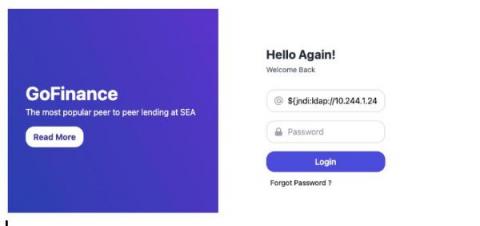
Spotting Log4j traffic in Kubernetes environments
Editor’s note: This is the latest in a series of posts we have planned over the next several weeks where we explore topics such as network monitoring in Kubernetes, using sidecars to sniff and tunnel traffic, show a real-world example of detecting malicious traffic between containers, and more! Please subscribe to the blog, or come back for more each week.
FTSE 100 credential theft study 2022
Corporate credential theft is a targeted effort and makes FTSE 100 companies credentials particularly attractive to cybercriminals with accelerated digital transformation (BYOD and hybrid working). Once an attacker gets hold of stolen user credentials and passwords, they can sell the credentials in the cybercrime underground or use them to compromise an organization’s network, bypassing security measures and threaten the credibility and integrity of the institution.
The Future of AIOps
Impact Analysis: RubyGems Critical CVE-2022-29176 Unauthorized Package Takeover
On May 6, 2022, a critical CVE was published for RubyGems, the primary packages source for the Ruby ecosystem. This vulnerability created a window of opportunity for malicious actors to take over gems that met the following criteria: Because RubyGems provides data dumps that include a lot of information, it is unfortunately relatively simple to create an automated mining process for these criteria.
What to look for in a vCISO as a service
“Approximately 64% of global CISOs were hired from another company” according to the 2021 MH Global CISO Research Report. The reasons are because of talent shortages, the role is still new to some companies, and companies have not created a succession plan to support internal promotions. To overcome these challenges, companies can look to Virtual Chief Information Security Officer (vCISO) or a vCISO as a service provider.
Municipal Cybersecurity Plan: Top 5 Factors to Incorporate
Cyber attacks on state and local governments continue to be on the rise. With more attacks targeting municipalities, there needs to be a push toward boosting cyber preparedness. Even though the risks remain at an all-time high for municipalities, the lack of budget and knowledge has caused officials to put cybersecurity on the back burner.