Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
How Should Employees Be Trained for Cyber Security?
Cyber security risks have never been more apparent and costly. According to the survey data, the average cost to the U.S. organizations that experienced a cybersecurity breach in 2020 was approximately 8.64 million dollars per incident, up almost a half-million dollars from 2019. Rates of cyber security attacks and identity theft have significantly increased and seem to be only becoming easier for hackers and cybercriminals.
Announcing Keeper One-Time Share
Ever need to share a password with someone, maybe a friend, a contractor or a business associate but they don’t have a Keeper account? Keeper is pleased to announce the launch of One-Time Share, a new feature that lets Keeper users securely share records with anyone on a time-limited basis, without the recipient having to create a Keeper account.
Stories from the SOC - Command and Control
Once a malicious actor has gained initial access to an internal asset, they may attempt to conduct command and control activity.
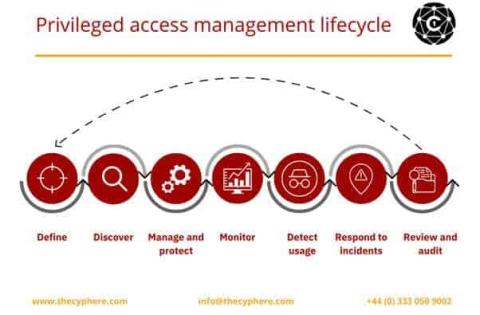
What is Privileged Access Management (PAM)?
Privileged account management is the process of identifying, controlling and monitoring privileged accounts and their associated activity. Privileged accounts are typically high-level administrator accounts that have broad access rights across an organisation’s IT systems. Because of their elevated level of access, these accounts pose a significant risk if they were to fall into the wrong hands.
Q1 2022 Threat Landscape Briefing: Threat Actors Target Email for Access and Extortion
What is the NIST Supply Chain Risk Management Program?
NIST (National Institute of Standards and Technology) is a federal agency under the responsibility of the US Department of Commerce. Established in 1901 to promote innovation and industrial competitiveness in the US, NIST helps organizations advance measurement science, technology, and standards to improve the quality of life for citizens and enhance economic security.
Why Risk Intelligence is Today's Top Security Priority
$132.94 billion. That’s the size of the cybersecurity market today. But despite the massive investment in money, time, and expertise, organizations have never been more at risk of an attack. What’s causing the disconnect? Despite all the effort to ensure security, there is an equally massive and growing effort to exploit vulnerable organizations.