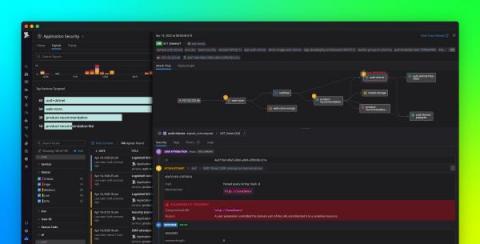
Introducing Datadog Application Security Monitoring
Securing modern-day production systems is expensive and complex. Teams often need to implement extensive measures, such as secure coding practices, security testing, periodic vulnerability scans and penetration tests, and protections at the network edge. Even when organizations have the resources to deploy these solutions, they still struggle to keep pace with software teams, especially as they accelerate their release cycles and migrate to distributed systems and microservices.