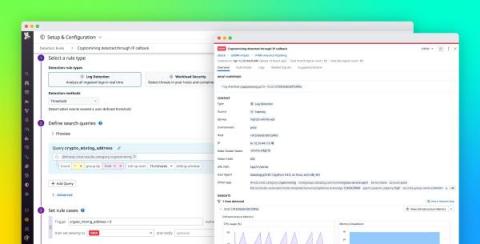
6 Best Practices for Kubernetes Audit Logging
Running a Kubernetes-based infrastructure is challenging and complex. Administrators often lament how complicated performance optimization and monitoring are, which can lead to problems in production. Additionally, even finely-tuned Kubernetes deployments can encounter sporadic issues. When Kubernetes starts behaving in strange ways, digging into logs can help you uncover breadcrumbs. These contextual hints can help lead you to possible solutions.